Data Privacy
i-doit i-doit Cloud / Paid
Extend i-doit with GDPR-relevant fields. The master data remain, the extended permission system ensures security.
-
Inventory Agent of SHD Connect | Checkmk delivers important foundation information for the IT asset management
-
PUSH / PULL procedure for bidirectional use of configuration data
-
New command line tool for automated data exchange via scripts and cron jobs.
-
Extended GUI for more overview about your IT infrastructure
Paid
Information on support options can be found on the developer website (DE only)
For installation instructions, please check the developer's website
Make your IT documentation fit for the GDPR
Step 1: Documentation and import of catalogues
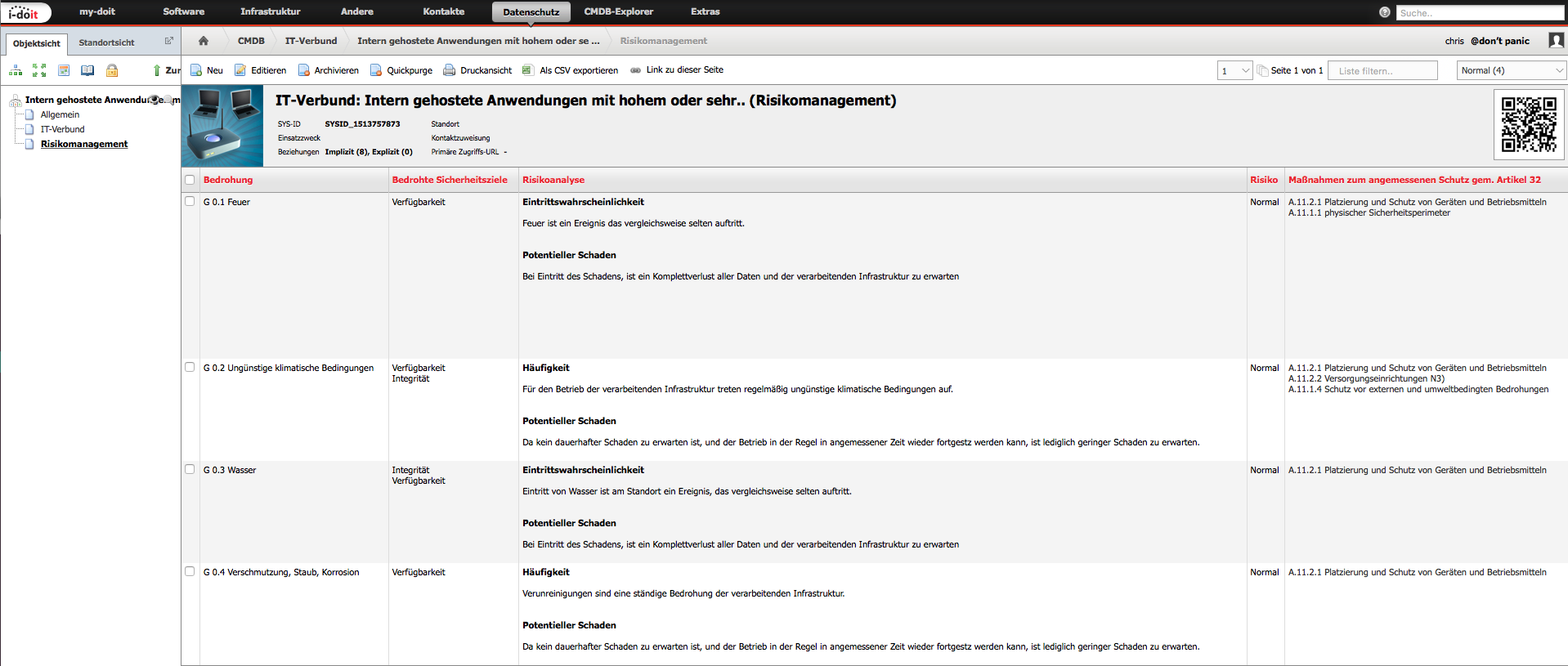
The directory of processing activities required by the GDPR (Article 30) can be usefully integrated into existing IT documentation. The Data Privacy add-on extends i-doit with specific object types and categories to help you fulfil your documentation and accountability obligations. At the same time, threat and action catalogues provide you with risk management support.
Step 2: Recording the processing activities
The second step towards compliance with the GDPR is the recording of processing activities, data subjects, categories of data processed, etc. The risk management is based on the technical and organisational measures planned and implemented to protect the processing activities. The basis of risk management, in which technical and organisational measures for the protection of processing activities are planned and implemented, is the definition of protection needs.
Step 3: Gap analysis and optimisation process
In the last step, you can use the documentation to create gap analyses of existing declarations of consent, reports on information obligations and contracts with processors. In the case of discrepancies, you can initiate a continuous optimisation process. The change management and request fulfilment processes are also supported by corresponding i-doit add-ons.
Why you need the Data Privacy add-on
Data protection is already an important topic for all companies. In 2018, IT managers were faced with far-reaching changes: the new EU General Data Protection Regulation (EU GDPR) has been in force since the 25th of May 2018. This replaces some of the principles of data protection law under the old BDSG.
The GDPR provides for the obligation to keep a register of processing activities with clearly defined minimum requirements. In addition, further documentation obligations are provided for.
The Data Privacy add-on creates the structure to include the mandatory content according to Article 30 of the GDPR and also to document information that data controllers need to fulfil their accountability obligations according to Article 5(2).
Use-Cases
.webp?width=300&name=multi-ethnic-colleagues-working-together-at-data-c-2025-03-15-19-35-44-utc%20(1).webp)
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Related Add-ons
Add-on für mächtige Datenanalyse. Berechnen Sie Servicekosten, prüfen Sie die Datenqualität der CMDB und führen Sie Ausfallsimulationen durch.
Erstellen Sie leistungsstarke Automatisierungen ohne Programmierkenntnisse ganz einfach nach einem Zeitplan oder manuell per Knopfdruck starten.
Bauen Sie ein Information-Security-Management-System mit Risikoanalyse und -management nach ISO 27001 auf.
Dokumente auch als PDF automatisch erstellen mit tagesaktuellen Daten (z.B. Hardware-Übergabeschein oder Desaster Recovery Plan).
Integrieren Sie das Monitoring-System Checkmk2 in i-doit. Abgleiche zwischen SOLL und IST aus CMDB und Monitoring werden damit unterstützt.
Erstellen Sie auf einfache Weise Formulare, die Sie Nutzern zur vereinfachten Dateneingabe zur Verfügung stellen. Beispiel: Hardware oder Waren selbst dokumentieren lassen.
Hinterlegen Sie Buttons mit eigenen Triggern und starten Sie IT-Prozesse direkt aus i-doit –z.B. das automatische Deployen einer virtuellen Maschine.
Mit diesem Add-on können Sie ein Managementsystem für die Informationssicherheit (ISMS) nach IT-Grundschutz-Methodik des BSI erstellen.
Get your personalized quote today!
Discover how the i-doit Add-on Data Privacy can support and streamline your processes. Get in touch with us for more information, pricing details, or to request a quote.

Telefon: +49 (0) 211 - 699 31 0