ISMS
Software, use cases & solutions
4.7/5 on Capterra | 2,000+ satisfied customers

What is an ISMS?
Introduction
An information security management system (ISMS) is a structured system of processes, guidelines and measures that companies use to systematically protect their information assets. It includes not only technical security mechanisms, but also organizational rules, responsibilities, risk assessments and continuous improvement processes.
The ISMS takes a holistic view of information - regardless of whether it exists digitally, physically, in processes or in the minds of employees. It defines which assets need to be protected, which risks exist, which protective measures are required and how their effectiveness is monitored.
The benefit: companies achieve a controlled, traceable and audit-proof level of security, reduce security risks, meet compliance requirements (e.g. ISO 27001, NIS2, BAIT) and improve their ability to respond to security incidents. A well-implemented ISMS ensures that information security is not a one-off project, but an ongoing and measurable management process that is supported by all relevant stakeholders.
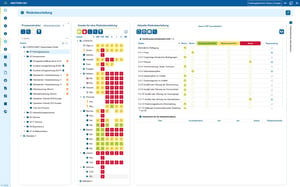
GRC use cases
Use cases relating to ISMS, risk and compliance management

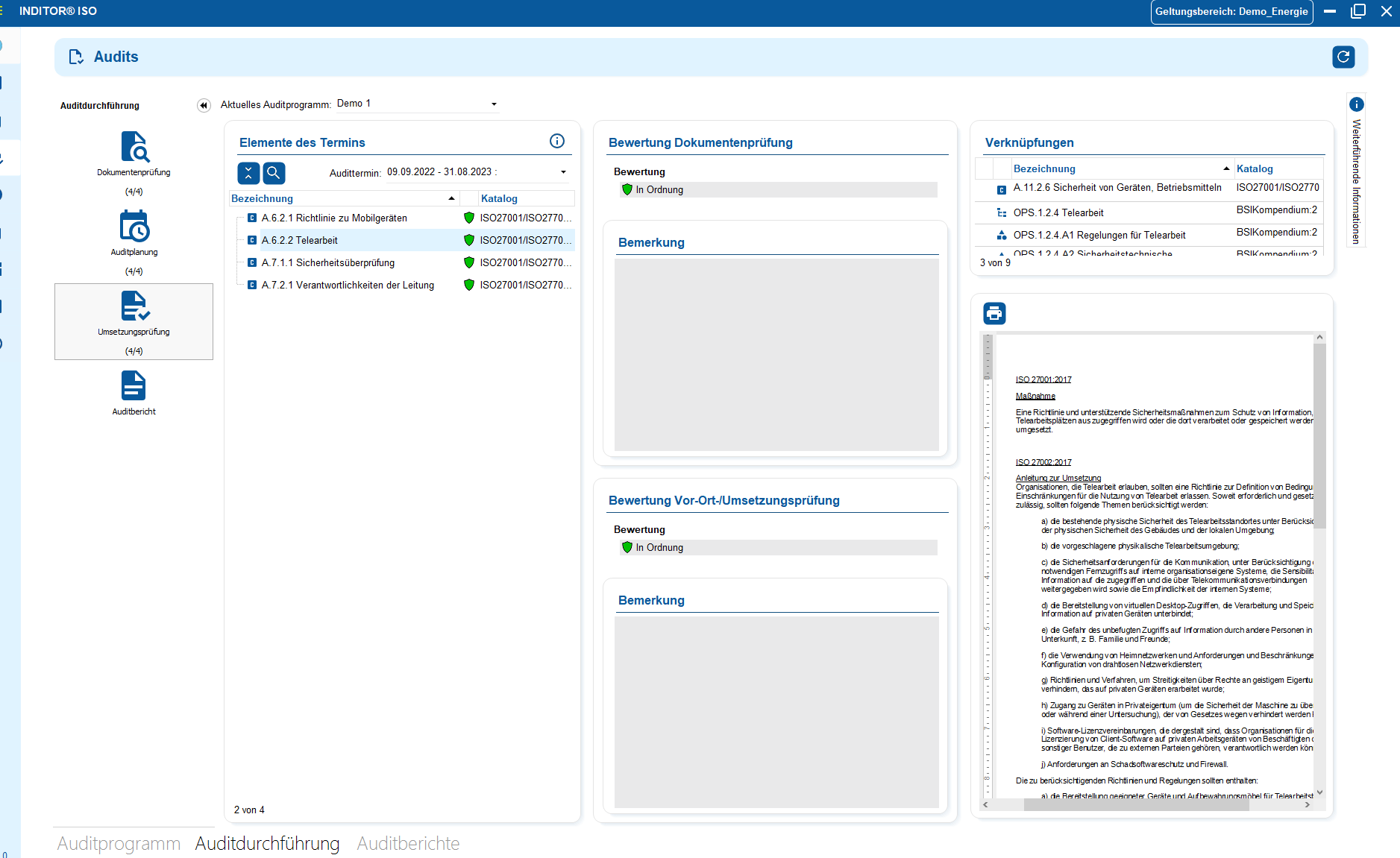
You control audits centrally, plan audits, document results and automatically generate audit reports.

You can manage documents in an audit-proof manner, version and edit them directly in the tool and use templates and import functions.

i-doit supports GAP analyses according to standards such as ISO 27001, ISO 9001 or NIS2, including maturity level assessment, responsibilities and document assignment.

You evaluate and manage suppliers centrally, document contracts and maintain contact details and replacement suppliers.

You derive measures, distribute tasks, track deadlines and receive automatic notifications by e-mail.

You document and evaluate security incidents in accordance with ISO and NIS2, assign affected assets and centrally derive measures.
Why an ISMS forms the basis for ISO 27001
Many companies face the challenge of setting up an ISMS from scratch. Often there is no central structure, responsibilities are unclear and risks or measures are only recorded in a fragmented manner.
i-doit solves precisely this problem by providing a clearly structured, logically linked and auditable information base. Risks, measures (TOMs), responsibilities, processes and assets are mapped uniformly - and provide the complete, comprehensible foundation that is essential for ISO 27001.
Advantages:
- Clear entry: A ready-made structure for risks, measures, responsibilities and documents - without any preparatory work.
- Complete traceability: Every measure, check and decision is automatically versioned and historicized.
- ISO-compliant process support: risk analysis, treatment, effectiveness testing and PDCA cycle are integrated and can be implemented without additional tools.
An ISMS based on i-doit logically maps all security-relevant information - risks, measures, processes, assets and responsible parties are seamlessly interlinked.
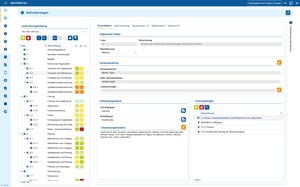
3 steps to an ISMS
and evaluate
and verify
manage
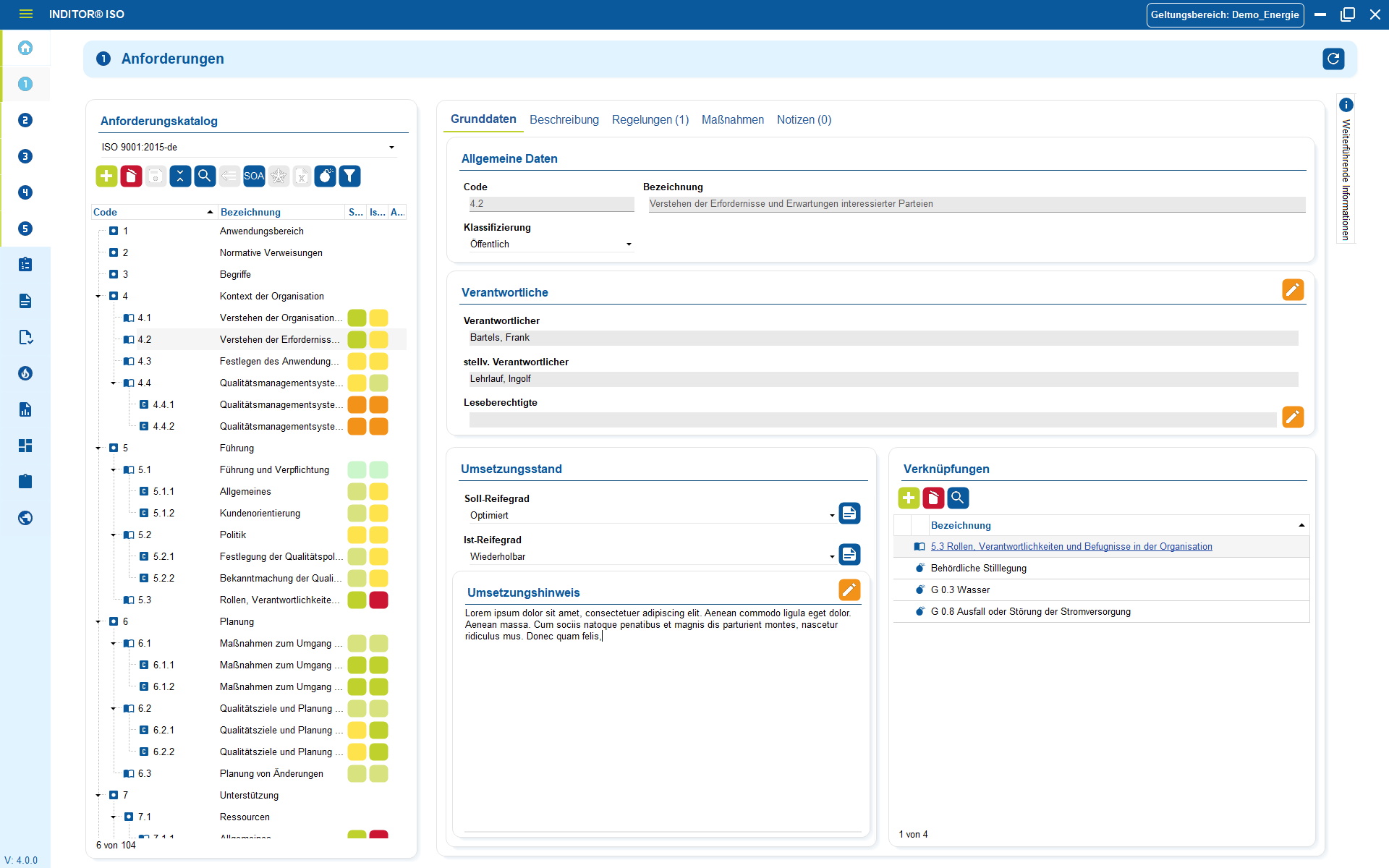
1 ISMS and asset management - identifying and assessing risks
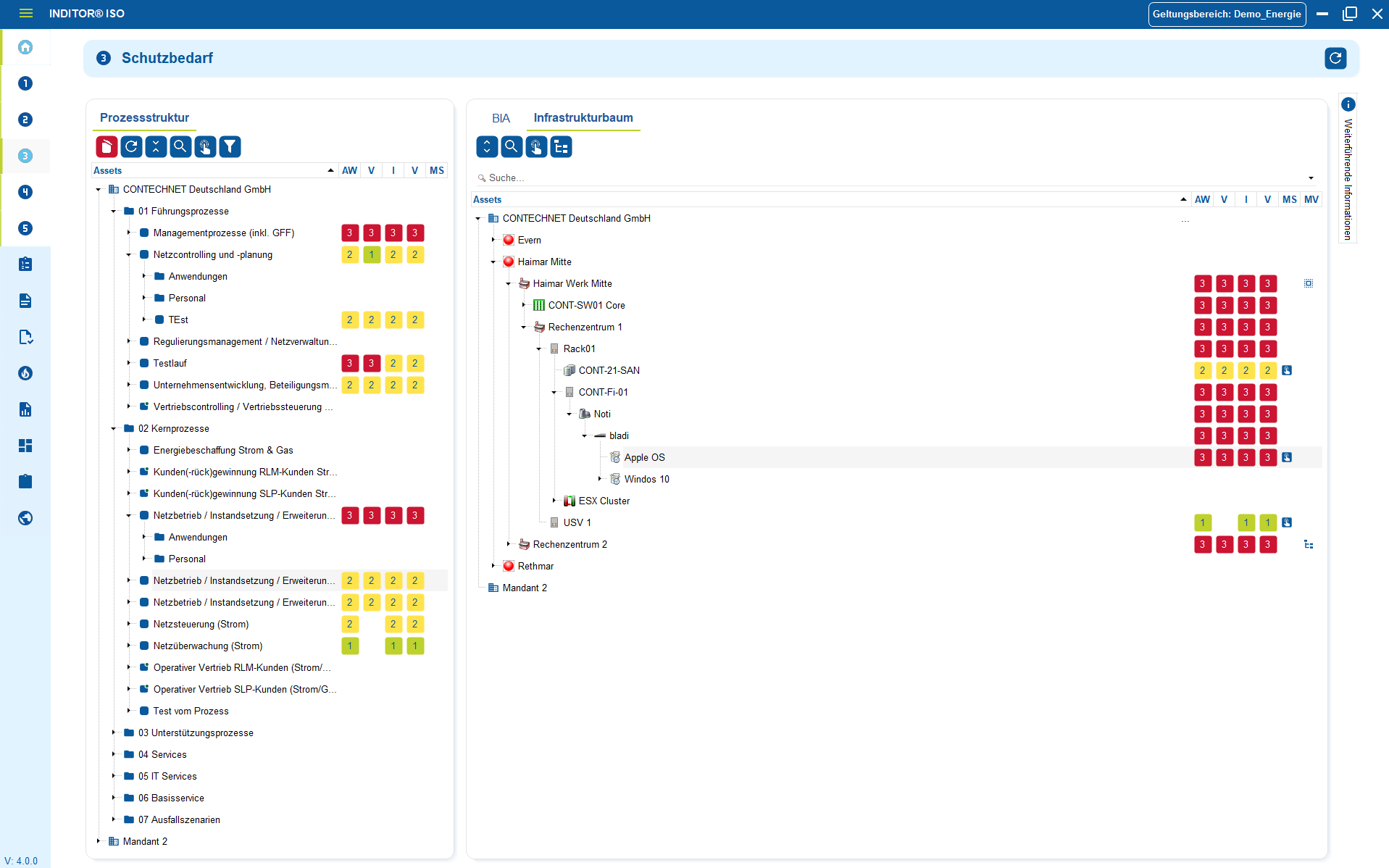
Asset management is a central element of ISO 27001: companies need to know what assets they have, where they are located, what protection they require and what risks are associated with them.
Our tools fully map these requirements by centrally recording and linking all relevant information values from servers, applications and data to locations, processes and responsibilities. Based on this, the risk analysis can be implemented.
Threats, vulnerabilities and impacts are applied directly to the respective assets, which means that the risk assessment is not abstract, but concrete and based on the actual system landscape.
Advantages:
- ISO-compliant asset management: all information values are recorded in full, in a structured manner and with responsibilities
- Risk assessment: Threats, vulnerabilities and impacts can be assessed directly on assets, processes or information classes.
- Annex A controls can be assigned: Measures (controls) from Annex A can be immediately assigned to the affected assets and risks.
- Integrated determination of protection requirements: Criticality, confidentiality, integrity and availability can be mapped centrally and are incorporated into the risk analysis.
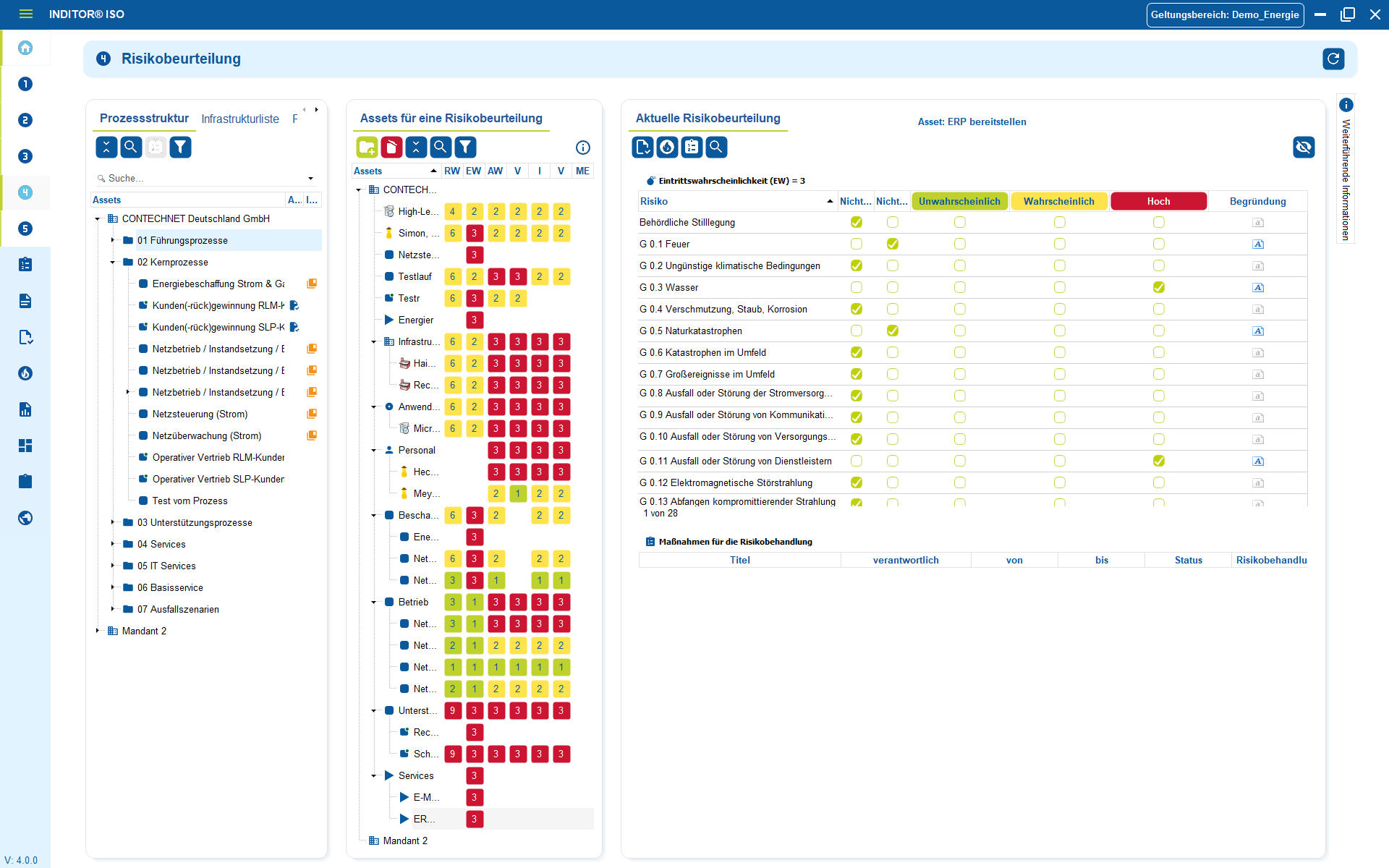
2. Plan, implement and verify measures
ISO 27001 requires that identified risks are dealt with by means of suitable measures. Measures from Annex A serve as the basis for this, which can be selected depending on the risk or supplemented by your own measures.
Our tools allow you to fully map this process: Measures are recorded in a structured manner, assigned to the relevant risks and assets and documented in an audit-proof manner. This makes it possible to see at any time which controls have been implemented, checked or are still open.
Advantages:
- Coverage of all Annex A controls: Measures can be structured and assigned directly in accordance with ISO 27001:2022.
- Audit-proof documentation: every change is historicized - ideal for internal and external audits
- Responsibilities & deadlines: Each control is assigned a responsible person, due dates and status
- Integrated effectiveness check: PDCA cycle with regular review and verification.
- Direct link to assets & risks: Measures do not take effect in the abstract - they are linked to the actual system or process.
3. Manage policies and procedures in an audit-proof manner
ISO 27001 requires structured, traceable and version-controlled documentation of all security-relevant information, from policies and guidelines to procedures, logs and evidence.
With our tools, these documents can be centrally managed, clearly assigned to responsible persons, versioned and directly linked to assets, risks and measures. This creates a consistent and auditable documentation basis that fully complies with the requirements of ISO 27001.
Advantages:
- Central storage of all ISMS documents: policies, guidelines, procedures, protocols and work instructions in one place.
- Versioning & historization: Changes are stored in an audit-proof manner, including responsible persons and time stamps.
- Evidence management for audits: Processes, decisions and measures can be fully traced.
- Link to assets, risks and controls: Documents are not isolated, but in the context of the actual IT and process landscape.
Industries
View all solutions for your industry



Read more




Example use cases for an ISMS
assets
and system manuals
management
management
and access
1. Import of existing assets
Many companies already have data on systems, applications, locations, contracts or responsibilities. However, it is often scattered across Excel lists, internal repositories, monitoring information or previous inventories. Instead of manually entering this information again, existing structures can be adopted and integrated into a central information security architecture.
The import enables an orderly consolidation of all relevant assets - from technical components, cloud services and process data to roles and responsibilities. During the import process, the data is classified, responsibilities are assigned and dependencies are made visible.
On this basis, protection requirements can be determined, risks assessed and suitable measures assigned in accordance with ISO 27001.
Advantages:
- No starting from scratch: existing information is transferred instead of newly recorded
- Transparency: assets, responsibilities and dependencies are clearly visible
- Structure: classification, protection requirements and risks can be assigned directly
- Traceability: changes are versioned and documented for auditing purposes
- Future-proof: repeatable imports avoid data silos and duplicate maintenance
2. IT concepts, emergency and system manuals
Create, link and maintain operational and emergency documentation in a structured and audit-proof manner.
With our tools, you can create and maintain all important technical documentation in a complete, up-to-date and audit-proof manner. Data changes are automatically transferred to emergency and system manuals, operating concepts and guidelines. These can be linked directly to the associated assets, processes and locations. This means that all documentation is automatically fed with real statuses from the IT landscape and remains permanently consistent.
All relevant information such as responsibilities, operating parameters, dependencies, restart processes and recovery times (RTO/RPO) are maintained and versioned centrally. The connection to infrastructure, applications and services means that documentation is not only maintained, but actively lived and constantly kept up to date. This is one of the most important factors for audits, certifications and operational stability.
Advantages:
- Centralized, versioned and audit-proof documentation
- Clear responsibilities and traceable operating processes
- Audit and audit-proof evidence in accordance with ISO 27001, NIS2 and BSI requirements
- Faster restart times in an emergency thanks to clear, always up-to-date instructions
- Transparent dependencies between systems, processes and services

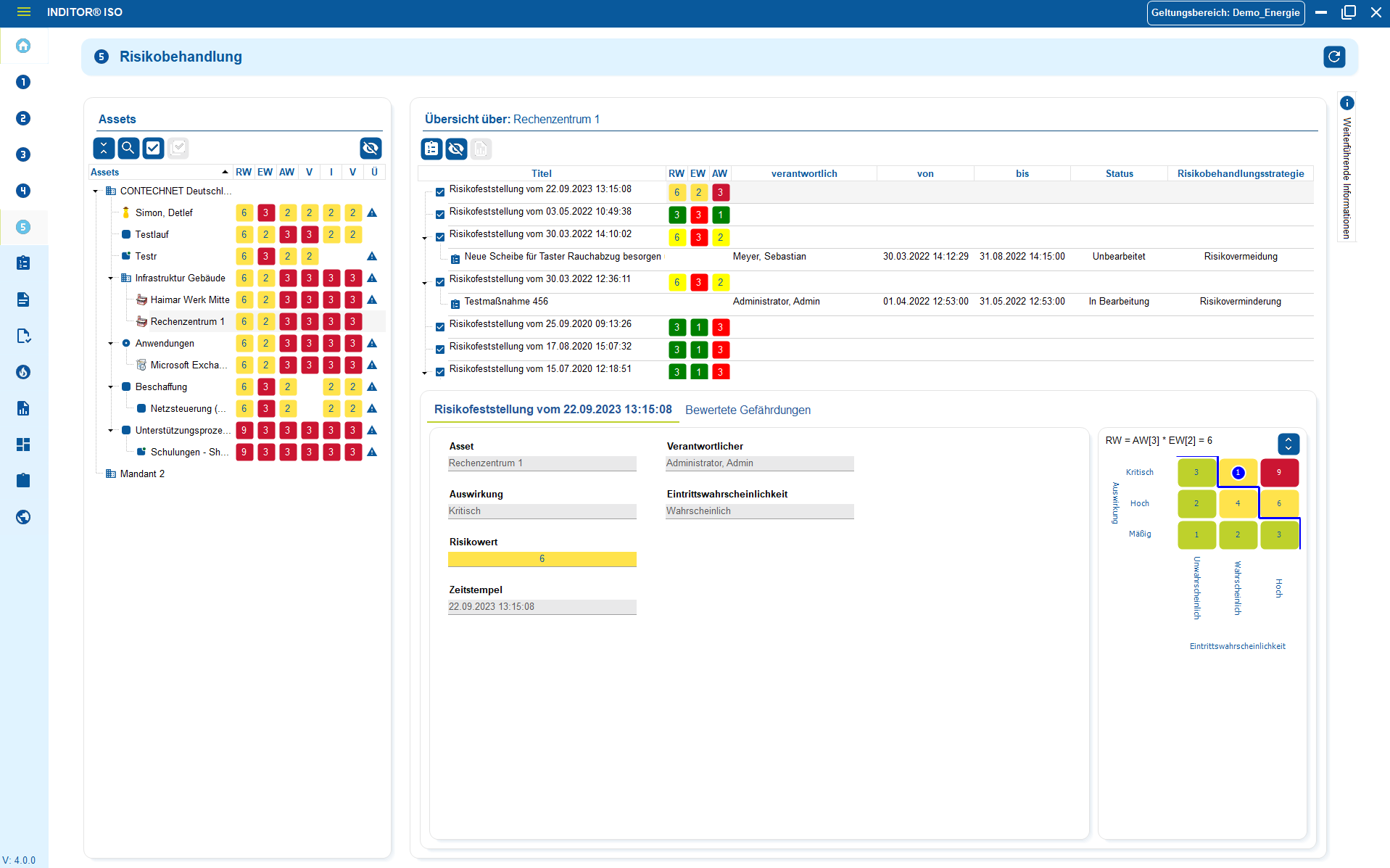
3. Security incident management
Link processes and associated assets
Control IT service processes efficiently and transparently. With the integration of ticket systems in i-doit, you can bundle all processes in one place. From fault reports and change requests to service requests. The link to your assets, contracts and responsibilities creates a central information base for the entire IT operation.
Tickets are documented in a traceable manner, automatically classified and can be prioritized, delegated and closed using defined workflows. This creates a smooth process between technology, organization and support.
Advantages:
- Standardized control of all IT processes
- Clear responsibilities and faster response times
- Seamless traceability of changes and measures
- Direct connection to CMDB objects and documentation
- Basis for key figures, evaluations and process optimization
4. Supplier management
External service providers, hosting providers, maintenance partners or cloud services are often directly involved in critical business processes. Structured supplier management makes it possible to map their services, risks, contracts and dependencies centrally. Responsibilities, service levels, security requirements and effects on information assets are documented in a traceable manner and linked to the relevant processes and measures.
This allows companies to retain control over which suppliers have access to which information assets, which requirements apply and whether agreed protective measures are being adhered to
Advantages:
- Transparency across all security-relevant suppliers and service providers
- Traceable assignment to assets, processes, locations and risks
- Clear responsibilities, competencies and service levels
- Contractual security requirements and compliance specifications can be documented centrally
- Ready to provide evidence for audits, certifications and regulatory checks

5. Precisely control the distribution of tasks and access to information
A functioning ISMS requires clear responsibilities. Who evaluates measures, who releases risks, who is allowed to change guidelines or who is only allowed to read - all of this determines security, efficiency and auditability.
Finely granulated role and authorization concepts clearly assign responsibilities: Teams, departments and individuals are given exactly the access they need for their tasks. Sensitive information remains protected, operational processes remain transparent and evidence is not diluted.
Advantages:
- Clear responsibilities: Roles and tasks are clearly assigned - no gray areas or duplication of responsibilities.
- Finely granulated access control: Authorizations for objects, categories and processes can be precisely defined.
- Protection of sensitive information: Critical data is only visible and editable for authorized users.
- Auditability through traceability: every action can be traced back in terms of time, organization and personnel.
- Reduced errors and misunderstandings: Teams only work with the information they really need.

.png?width=300&name=Contact%20(1).png)
Book your personal live demo
Our i-doit team will be happy to take the time to advise you personally on your application.
Suitable add-ons
Our add-ons for modular function expansion
Create powerful automations without programming knowledge, simply start them on a schedule or manually at the touch of a button.
Get 4 powerful add-ons for the price of 2! Flows, Documents, Analysis and Forms.
Automatically create documents as PDFs with daily updated data (e.g. hardware handover certificate or disaster recovery plan).
Automate the operation of your data center with the latest data from the CMDB. Events trigger and control further processes.
The maintenance add-on supports the planning, execution and documentation of maintenance and inspections. Maintenance intervals, dates and responsibilities are managed centrally and linked directly to the respective devices, installations or systems.
With the API add-on, data can be automatically read, written and updated in i-doit. Perfect for integrations with ticket systems, inventory tools or your own automations.
Add-on for powerful data analysis. Calculate service costs, check the data quality of the CMDB and carry out failure simulations.
Easily create forms that you can make available to users for simplified data entry. Example: Allow users to document hardware or goods themselves.
Set up an information security management system with risk analysis and management in accordance with ISO 27001.
Integrate the Checkmk2 monitoring system into i-doit. This supports comparisons between TARGET and ACTUAL from CMDB and monitoring.
Store buttons with your own triggers and start IT processes directly from i-doit - e.g. the automatic deployment of a virtual machine.
With this add-on, you can create an information security management system (ISMS) in accordance with the BSI's IT baseline protection methodology.




