
BSI-Standard 200-4: Business Continuity Management
What is Business Continuity Management?
Business continuity management (BCM) is a holistic management process that aims to strengthen the resilience of organizations to potential threats and ensure the continuity of critical business processes.
It includes the identification of potential risks, the development of strategies to minimize their impact and the planning of measures to quickly restore normal operations in the event of an interruption. BCM goes beyond pure emergency planning. It integrates preventive measures, crisis management and recovery processes into a systematic approach.
The aim of strategic BCM is to increase the organization's resilience and reduce potential economic and reputational damage. In an increasingly networked business world characterized by security threats, BCM has become an indispensable component of modern corporate management.
Introduction to the BSI Standard 200-4
The BSI Standard 200-4 was published by the German Federal Office for Information Security (BSI) on June 14, 2023 and provides practical guidance for setting up and operating a business continuity management system (BCMS).
It replaces the previous Standard 100-4 and has been comprehensively modernized. The standard aims to help institutions of all sizes and from all sectors to prepare for emergencies and crisis situations.
A key feature of the standard is the three-stage BCMS model, which makes it easier for both inexperienced and experienced users to get started. The standard also highlights potential synergies with other management systems.
The BSI Standard 200-4 provides a manageable, flexible and adaptable solution that meets the increased requirements for strategic business continuity processes.
Source: Federal Office for Information Security
BSI Standard 200-4 vs. 100-4: The most important differences
BSI Standard 200-4 replaces the previous Standard 100-4 and introduces significant innovations for business continuity management.
Three-stage BCMS model
A key feature of the new standard is the modular tier model. It allows organizations to enter flexibly, depending on their experience and resources. From a reactive BCMS (basic level) to an advanced BCMS to a comprehensive standard BCMS, companies can gradually expand their business continuity management. This structure makes the standard particularly user-friendly for organizations of different sizes and complexity.
Integration of management systems
The 200-4 standard integrates business continuity management more closely with other management systems, in particular information security management (ISMS). This integration makes it easier for organizations to exploit synergies between BCM and other areas such as IT security management or risk management. As a result, BCM is no longer viewed in isolation, but as part of a holistic approach to increasing resilience.
Expanded methodology and practical relevance
The new standard offers a much more comprehensive and practical methodology than its predecessor. The Business Impact Analysis (BIA) has been expanded to take into account not only time-critical processes, but also resource-side dependencies in a more targeted manner. The standard is also more closely aligned with international standards such as ISO/IEC 22301:2019. These adjustments make the standard more modern and relevant for current threat scenarios such as cyber attacks, natural disasters and global supply chain disruptions.
BCM and information security
The interaction between business continuity management and information security management is a key element of comprehensive organizational resilience. While the ISMS ensures the protection of information during normal operations, BCM ensures that critical business processes are maintained in crisis situations.
The BSI Standard 200-4 promotes this synergy through specific starting points:
- Shared use of resources: risk assessments and protective measures from the ISMS can complement BCM strategies, especially for IT-supported processes.
- Mutual process optimization: The BCM business impact analysis identifies critical business processes and their dependencies, which provides valuable insights for the ISMS.
- Integrated IT contingency planning: IT service continuity management (ITSCM) combines preventive ISMS measures with the restart and emergency strategies of BCM.
This integration creates a consistent strategy for dealing with threats such as cyber attacks or system failures. It improves the use of resources and strengthens the organization's overall risk management.
Business processes in BCM
Critical business processes are at the heart of BCM, as their failure can quickly lead to significant financial, regulatory or reputational damage. The Business Impact Analysis (BIA) identifies and prioritizes these processes, determines their Maximum Tolerable Period of Disruption (MTPD) and Recovery Time Objective (RTO) and derives targeted measures for risk minimization and recovery.
BCM not only considers the main processes, but also the associated resources such as IT systems, personnel and external service providers. BSI Standard 200-4 provides a clear structure for the analysis and recommends an appropriate level of detail in order to keep the effort efficient without losing the overview.
A central component of the standard is the regular review and optimization of the defined measures through training, simulations and emergency tests. These help to identify weaknesses and continuously improve the BCM strategy. The standard also requires that business process continuity planning is regularly reviewed and adapted to new threat scenarios such as cyber attacks or natural disasters.
Interruptions to business processes
In the context of business continuity management, BSI Standard 200-4 distinguishes between different escalation levels of interruptions: Disruption, Emergency and Crisis. This differentiation is crucial for an appropriate response and management of events that jeopardize business operations.
- Disruption: A disruption is a minor impairment of a business process that can be rectified with existing resources and without major intervention. Examples include temporary IT failures or delays in supply chains.
- Emergency: An emergency requires the activation of specific contingency plans as it threatens critical business processes. Typical scenarios include prolonged IT outages, staff shortages or significant infrastructure damage.
- Crisis: A crisis represents the highest level of escalation and threatens the existence of the entire organization. It requires strategic decisions at management level as well as comprehensive internal and external communication. Examples include natural disasters, cyber attacks or massive reputational damage.
BSI Standard 200-4 emphasizes the importance of clear escalation levels in order to initiate suitable measures at an early stage and ensure business continuity.
To manage these escalation levels, the standard distinguishes between the general organizational structure (AAO) and the special organizational structure (BAO). The AAO is responsible for normal operations and dealing with disruptions, while the BAO is activated in emergencies and crises. The BAO is a temporary form of organization with adapted responsibilities, hierarchies and communication and decision-making channels in order to be able to react quickly and effectively to extraordinary situations.
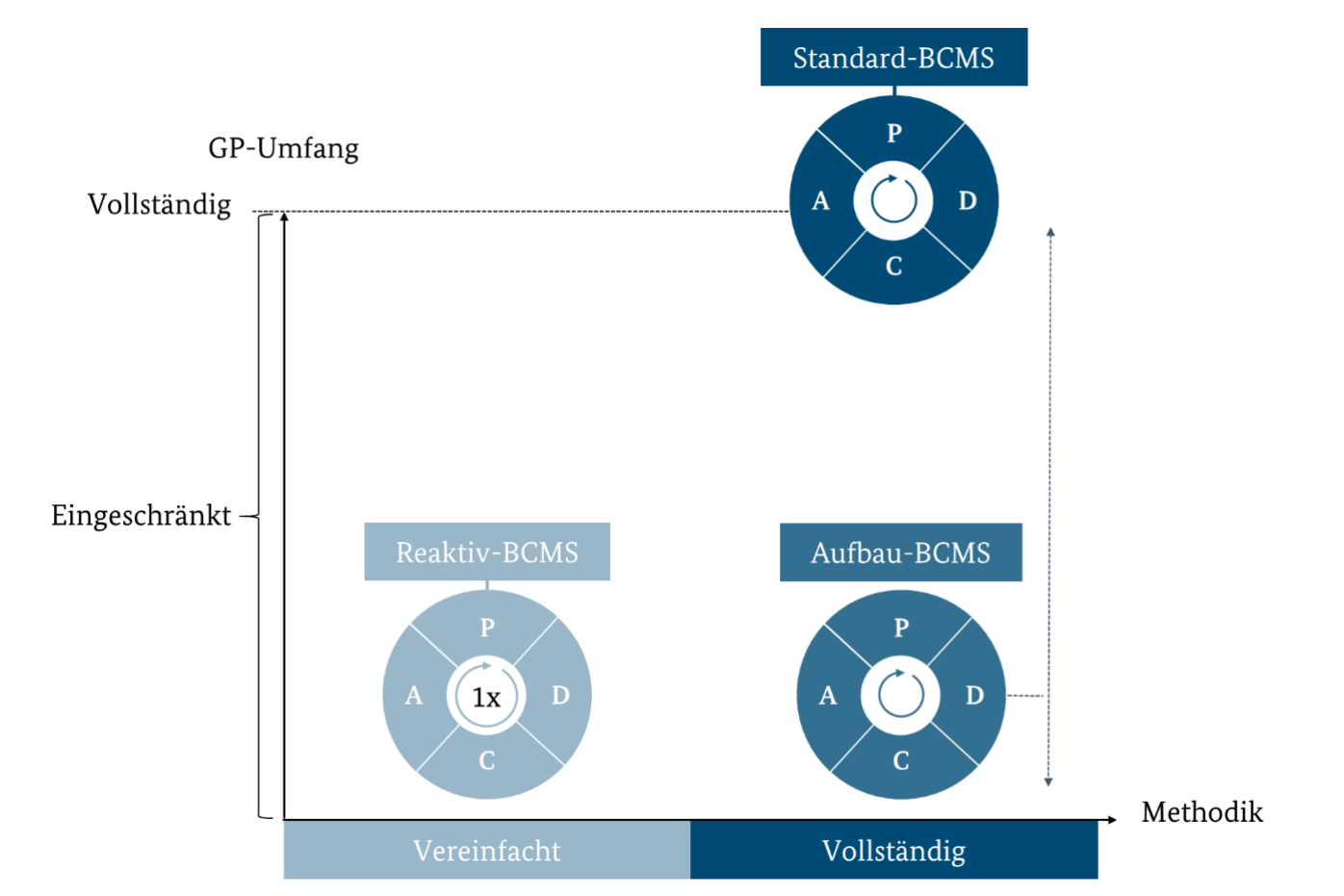
The three-stage BCMS model
BSI Standard 200-4 describes a three-stage BCMS that enables organizations to implement a flexible and scalable system. It takes into account different time, financial and personnel resources as well as the individual maturity level of the organization.
Reactive BCMS
This entry level is aimed at organizations that want to ensure a basic ability to respond to emergencies. It is based on existing security and precautionary measures and focuses on securing selected time-critical business processes with minimal effort. Further analyses, such as a comprehensive BIA, are carried out at a reduced level or downstream. The reactive BCMS serves as a simplified entry-level solution and can be further developed into a build-up or standard BCMS as required.
Advanced BCMS
The build-up BCMS extends the protection of time-critical business processes through more detailed analyses and structured measures. The scope of the BCMS is expanded step by step, with the most critical processes and resources being considered first. It is suitable for organizations that build up their BCMS over several cycles in a risk-oriented manner or have little previous experience.
Standard BCMS
The standard BCMS is a fully integrated BCMS. It includes a comprehensive analysis and safeguarding of time-critical processes, taking into account failure risks, dependencies and necessary resources. When fully implemented, it can meet the requirements of ISO 22301 certification, as the BSI Standard 200-4 is designed to be compatible with international standards in many areas.
The three-stage model not only offers a flexible introduction, but also supports organizations in gradually developing their BCM and adapting it to changing requirements or resources.
The three-stage BCMS model
Source: Federal Office for Information Security
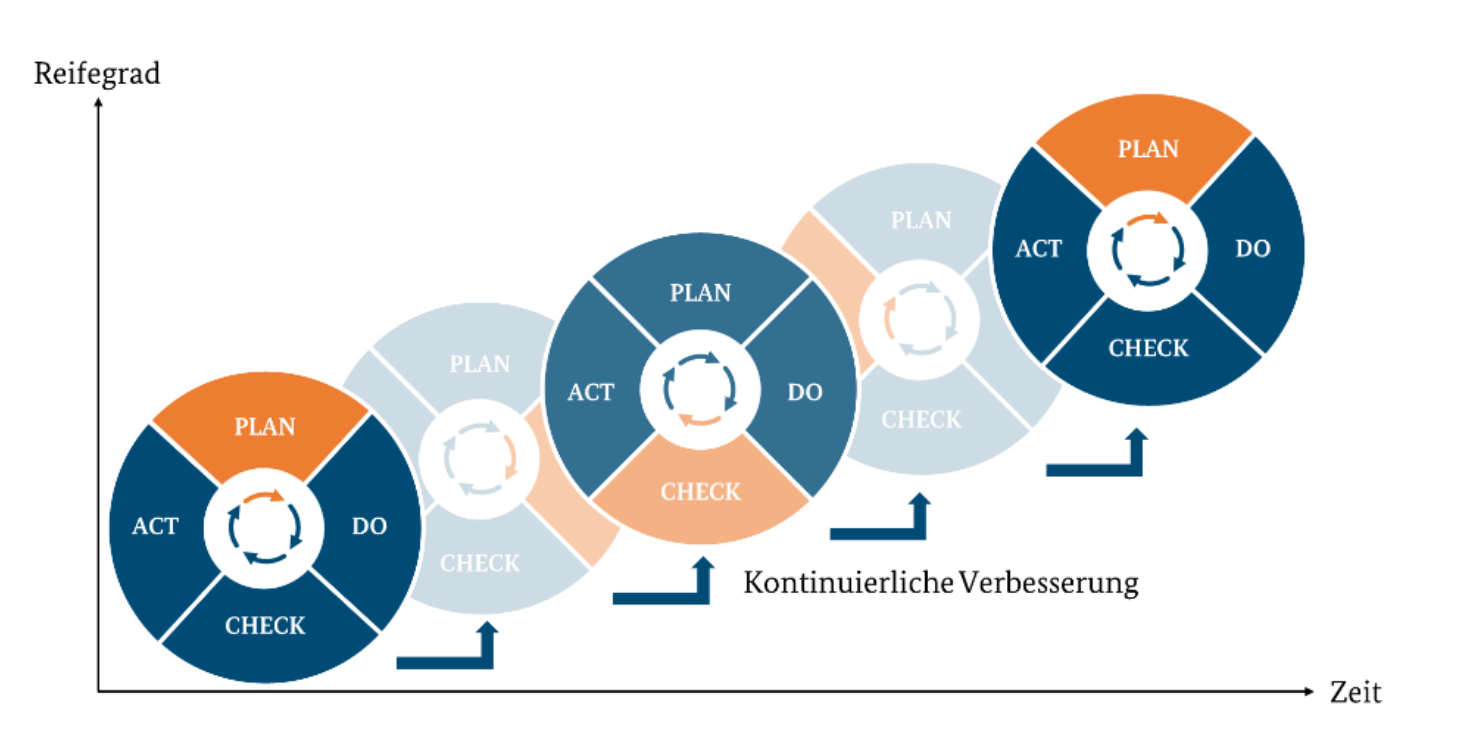
BCM process according to the PDCA cycle
The BSI Standard 200-4 is based on the proven PDCA cycle (Plan-Do-Check-Act) for the implementation and continuous improvement of the BCMS. This systematic approach ensures a structured and effective implementation of BCM in four phases:
Plan:
In this phase, the foundations for the BCMS are laid. This includes determining the scope, defining objectives and carrying out a business impact analysis and a BCM risk analysis. Based on these findings, BCM strategies are developed and a BCM concept is created that defines measures to safeguard time-critical business processes.
Do (implement):
This is where the concrete implementation of the planned measures takes place. This includes the creation of business continuity plans, the introduction of emergency precautions and restart measures as well as training and sensitization of employees to prepare them for an emergency.
Check:
In the review phase, the implemented measures are examined for their effectiveness. This is done through regular tests, exercises and audits. In addition, key performance indicators (KPIs) are monitored and compliance with legal and regulatory requirements is checked.
Act (Improve):
This phase is used for continuous improvement. Findings from the review are incorporated into the optimization of the BCM strategy and the adaptation of emergency plans. Processes are updated in order to be able to react to changing threat situations or organizational developments.
Thanks to the ongoing PDCA cycle, the BCMS remains adaptable and continues to evolve in order to ensure the long-term protection of critical business processes.
Source: Federal Office for Information Security
Integration of BCM into the organizational structure
The successful implementation of BSI Standard 200-4 requires a deep integration of business continuity management into the entire organization. An isolated approach is not enough - BCM must be strategically anchored, networked with existing management systems and integrated into day-to-day operations.
Strategic anchoring by top management
The starting point is top management, which defines the BCM strategy, provides resources and actively drives its implementation. Without clear support from top management, BCM often remains a purely operational issue without strategic penetration. This is why managers are not only responsible for approving budgets, but also for anchoring BCM as an integral part of corporate management.
Synergies with existing management systems
Effective integration is achieved through close dovetailing with existing management systems. In information security management, risk analyses and protective measures can be used jointly, while risk management enables a holistic risk assessment through coordinated evaluations. Quality management also benefits when BCM processes are integrated into existing standards.
Cross-departmental coordination and collaboration
Cross-departmental cooperation is just as crucial. A central BCM officer coordinates the measures, ensures uniform standards and makes sure that critical business processes and all relevant dependencies are taken into account. Specialist departments must be actively involved as they have the specific knowledge about processes, resources and potential weak points.
Establishing a BCM culture
Anchoring BCM in the corporate culture plays another key role. Regular training and practical exercises ensure awareness among employees and make BCM an integral part of daily activities. Transparent communication of objectives and expectations helps to create acceptance and promote commitment.
This holistic integration not only strengthens the company's resilience, but also enables a rapid and coordinated response to incidents. BCM is therefore not seen as an isolated measure, but as a strategic instrument for ensuring business continuity.
Practical tools for implementing the 200-4 standard
Various practical tools are available to organizations to support the implementation of BSI Standard 200-4.
The BSI itself offers a range of document templates and checklists that make it easier to get started with business continuity management. These include templates for business impact analysis, risk assessment and emergency plans.
There are also specialized software solutions that support the BCM process. For IT contingency planning in particular, there are tools that help to create, manage and update IT contingency plans and visualize dependencies between IT services and business processes.
Such solutions not only facilitate the initial implementation, but also support the continuous maintenance and improvement of the BCMS. They enable efficient documentation, simplify the execution of tests and exercises and support reporting to management.
Emergency planning with INDART Professional®
INDART Professional® simplifies the development and maintenance of process-oriented, intelligent emergency planning in real time through a structured and goal-oriented approach.
The advantages of our software solution at a glance:
- Mapping of complex dependencies between processes, IT infrastructure, application systems and responsible employees
- Wide range of import options and connection to existing systems
- Fast activation of restart procedures by a failure manager
- Representation of relevant business processes and the responsible personnel
- Analysis of head monopolies and missing infrastructure and redundancies
- Creation of an individual IT emergency and IT operating manual

Your Software for ISMS, Data Protection & GRC
Test the i-doit GRC Suite free for 30 days – in the cloud or on-premises.
More than 400 companies successfully manage information security, risks, and compliance with i-doit.




