Banks and insurance companies
- Software, use cases & solutions.
Complete, consistent and audit-proof IT documentation & GRC software implementation is not optional for banks and insurance companies, but a prerequisite for stable operations, regulatory evidence and audit-proof processes.
All technical, organizational and security-relevant information must be versioned and thus linked to one another.
4.7/5 on Capterra | 2,000+ satisfied customers

Use cases
i-doit use cases for your documentation needs

You document active and passive network elements including cabling, port assignment, IP addresses and configurations centrally and comprehensibly.

You record and analyze software and licenses, monitor runtimes, users and authorizations and avoid license violations and unnecessary costs.

You analyze your IT infrastructure, identify documentation gaps and create location, user or cost centre-related reports and audit PDFs.

You document and manage contracts centrally, link them to objects and responsible parties and are automatically informed about deadlines and terms.

They document maintenance and lifecycles, make changes traceable, automate processes and keep track of responsibilities and warranty periods.

You document locations, rooms and infrastructure, link these to contact persons and also visualize server rooms clearly.
Solutions for banks & credit institutions
Changes to systems, applications and processes in banks and credit institutions must be documented in a complete, comprehensible and audit-proof manner. i-doit maps all technical and organizational changes in a structured manner and provides a consistent basis for banking supervisory and auditing requirements.
Documentable:
- Changes to systems, applications, servers and core banking systems
- Process changes, technical adjustments, patches and deployments
- Release paths, change requests, approvals and risk assessments
- Dependencies between services, interfaces and locations
- Versioned histories, responsibilities and technical details
- Contracts, SLAs, service providers and contact persons
- Access rights and role models in the context of systems and processes
Advantages:
- Complete transparency of all changes in the IT landscape
- Audit-proof documentation in accordance with BAIT, MaRisk and ISO 27001
- Comprehensible change processes with clear responsibilities
- Consistent collaboration between IT, compliance, audit and specialist departments
Solutions for insurance companies
Insurers must provide special protection for sensitive customer, contract and service data. i-doit enables structured, versioned and clearly traceable role and authorization management across all relevant systems and applications.
Documentable:
- User roles, authorizations and access groups
- Assignment to applications, databases, services and clients
- Approval paths and responsibilities
- Recertification intervals and test logs
- Contracts, TOMs and data protection measures in accordance with GDPR & VAIT
- External partner access, service providers and interfaces
- Changes to role and authorization models
Advantages:
- Complete transparency of all access rights and authorizations
- Verifiable implementation of VAIT, GDPR, ISO 27001 and NIS2
- Reduction of incorrect authorizations and security risks
- Clear responsibilities and documented approval processes
- Support for recertifications and audits
- Structured overview for IT, compliance, data protection and specialist departments
Solutions for health insurance companies
Health insurance companies require audit-proof, centrally available and traceable documentation on IT, processes, contracts, guidelines and technical components. i-doit maps all documentation-relevant elements centrally, versioned and linked.
Documentable:
- Documents on processes, guidelines, security specifications and work instructions
- IT manuals, operating concepts, network and system overviews
- Contracts, service agreements, test protocols
- Knowledge articles on applications, internal processes and systems
- Technical assets, locations, server rooms and infrastructure
- Responsible persons, service providers, contact persons
- TOMs and regulatory evidence (ISO, GDPR, GKV requirements)
Advantages:
- Complete transparency across all technical and organizational documents
- Structured knowledge management for IT, specialist departments and auditing
- Audit-proof, versioned storage of all important documents
- Reduced effort for audits, checks and verifications
- Clear assignment of responsibilities, contracts and assets
- Improved collaboration between IT, data protection and specialist departments
Suitable add-ons
Our add-ons for modular function expansion
Create powerful automations without programming knowledge, simply start them on a schedule or manually at the touch of a button.
Get 4 powerful add-ons for the price of 2! Flows, Documents, Analysis and Forms.
Automatically create documents as PDFs with daily updated data (e.g. hardware handover certificate or disaster recovery plan).
Automate the operation of your data center with the latest data from the CMDB. Events trigger and control further processes.
The maintenance add-on supports the planning, execution and documentation of maintenance and inspections. Maintenance intervals, dates and responsibilities are managed centrally and linked directly to the respective devices, installations or systems.
With the API add-on, data can be automatically read, written and updated in i-doit. Perfect for integrations with ticket systems, inventory tools or your own automations.
Add-on for powerful data analysis. Calculate service costs, check the data quality of the CMDB and carry out failure simulations.
Easily create forms that you can make available to users for simplified data entry. Example: Allow users to document hardware or goods themselves.
Set up an information security management system with risk analysis and management in accordance with ISO 27001.
Integrate the Checkmk2 monitoring system into i-doit. This supports comparisons between TARGET and ACTUAL from CMDB and monitoring.
Store buttons with your own triggers and start IT processes directly from i-doit - e.g. the automatic deployment of a virtual machine.
With this add-on, you can create an information security management system (ISMS) in accordance with the BSI's IT baseline protection methodology.
.png?width=300&name=Contact%20(1).png)
Book your personal live demo
Our i-doit team will be happy to take the time to advise you personally on your application.
Applications for banks and insurance companies
(KRITIS, ISO27001 and NIS-2)
Central process control
Monitoring
Network inventory
Compliance (KRITIS, ISO27001 and NIS-2)
Ensure compliance with laws, standards and guidelines.
Secure critical infrastructures transparently. With i-doit, risks according to ISO 27001 can be systematically recorded, evaluated and linked to the affected assets. This creates a transparent basis for the verification of security measures and the implementation of NIS2 requirements. Technical and organizational measures (TOMs) are centrally documented, monitored and maintained in an audit-proof manner.
Advantages:
- Auditable infrastructure
- Audit-proof recording in accordance with NIS2 & ISO-27001 & BSI-KritisV
- Strengthening of information security
- Implementation of PDCA processes
- Faster response in the event of an incident or crisis
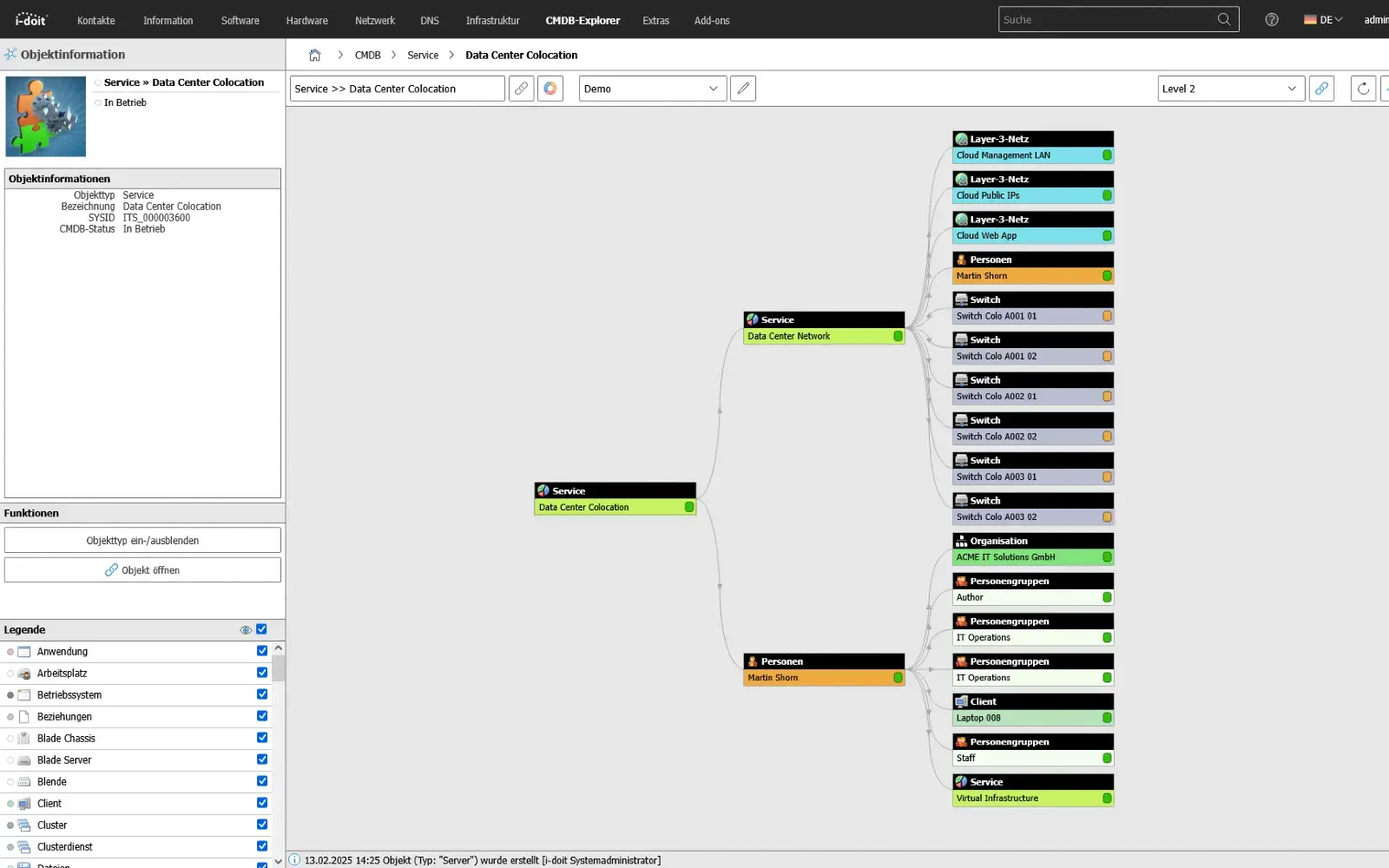
Ticketing - Central process control
Link processes and associated assets.
Control IT service processes efficiently and transparently. With the integration of ticket systems in i-doit, you can bundle all processes in one place. From fault reports and change requests to service requests. The link to your assets, contracts and responsibilities creates a central information base for the entire IT operation.
Tickets are documented in a traceable manner, automatically classified and can be prioritized, delegated and closed using defined workflows. This creates a smooth process between technology, organization and support.
Advantages:
- Standardized control of all IT processes
- Clear responsibilities and faster response times
- Seamless traceability of changes and measures
- Direct connection to CMDB objects and documentation
- Basis for key figures, evaluations and process optimization
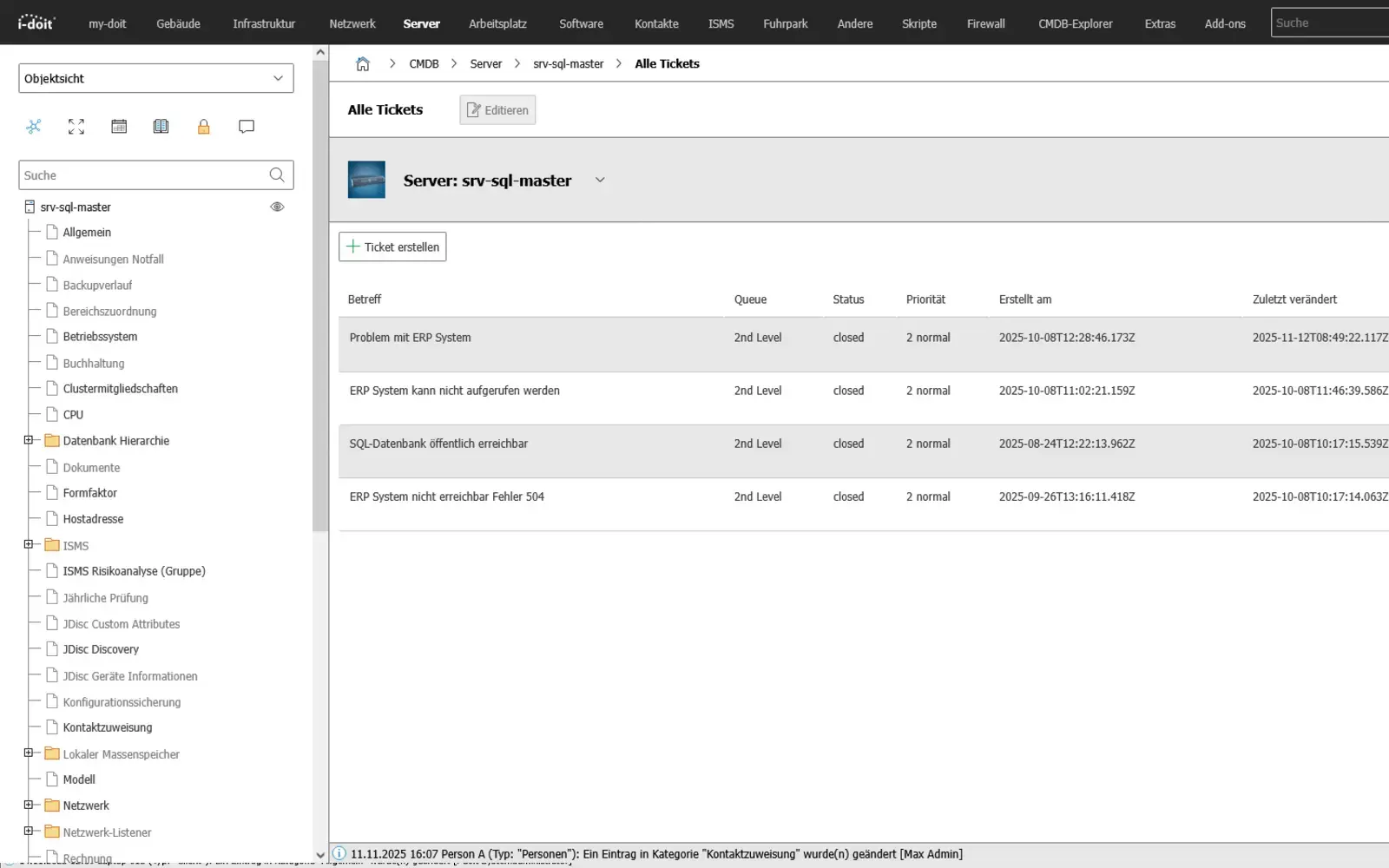
Live status from monitoring
Integrate live data into IT documentation
Efficient monitoring ensures that your IT systems are available and transparently documented at all times. With i-doit, monitoring data can be transferred directly into the CMDB. Devices, hosts and services are automatically synchronized and kept up to date. This gives you an overview of the status and life cycle of your entire infrastructure.
By linking monitoring information with the IT documentation, you can detect failures at an early stage, track changes to devices or services and analyze dependencies in a targeted manner. i-doit not only makes monitoring data visible, but also forms the basis for data-driven decisions.
Advantages:
- Automatic synchronization: Devices, hosts and services from monitoring are synchronized directly with the IT documentation - without duplicating maintenance effort.
- Up-to-date system overview: All status information, runtimes and changes are visible in the CMDB at all times.
- Fast error detection: Failures and faults are recorded immediately and displayed in the documentation.
- Life cycle transparency: Changes, maintenance and replacement times can be tracked seamlessly.
- Linked information: Monitoring data is in the context of services, contracts, locations or responsible parties.
- Better basis for decision-making: The combination of real-time data and documentation creates a complete picture of your IT landscape.
- Efficiency and compliance: Less manual work, reduced risk of errors and clean evidence for audits and certifications.
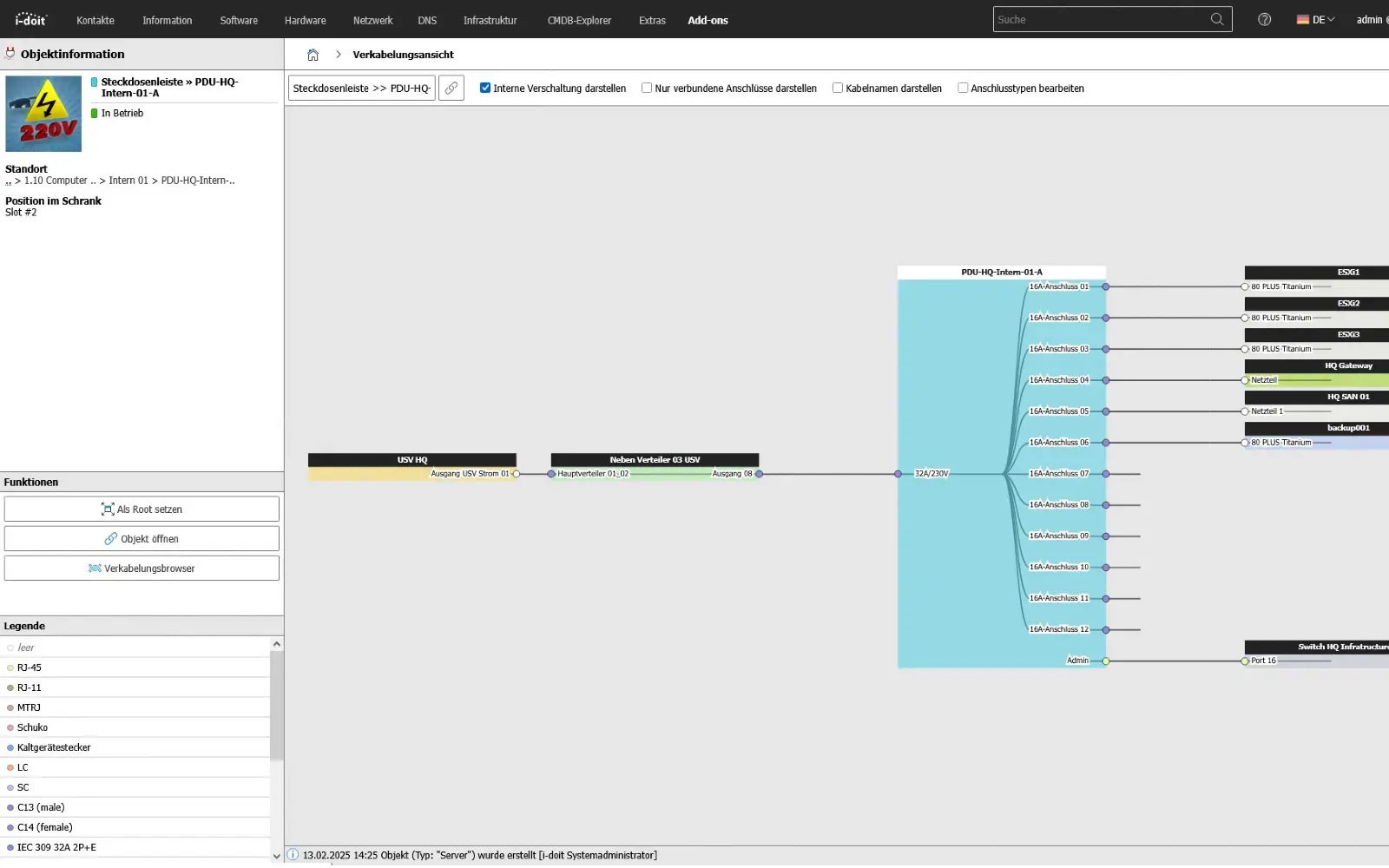
Automatic network inventory
Complete and up-to-date recording of IT infrastructure.
With the automatic network inventory, all devices, systems and software installations in your network are regularly detected, recorded and synchronized with i-doit. This creates an up-to-date and complete CMDB - without any manual effort.
By connecting tools such as JDisc, OCS Inventory or Baramundi, all relevant information - from hardware data and installed software to IP addresses and ports - can be centrally managed and evaluated. Changes in the network are automatically detected and documented in a versioned format.
Advantages:
- Complete and up-to-date IT database without manual effort
- Automatic detection of changes in the network
- Seamless integration with the i-doit CMDB
- Basis for audits, compliance and IT documentation
- Significant time savings for inventory and IT reporting
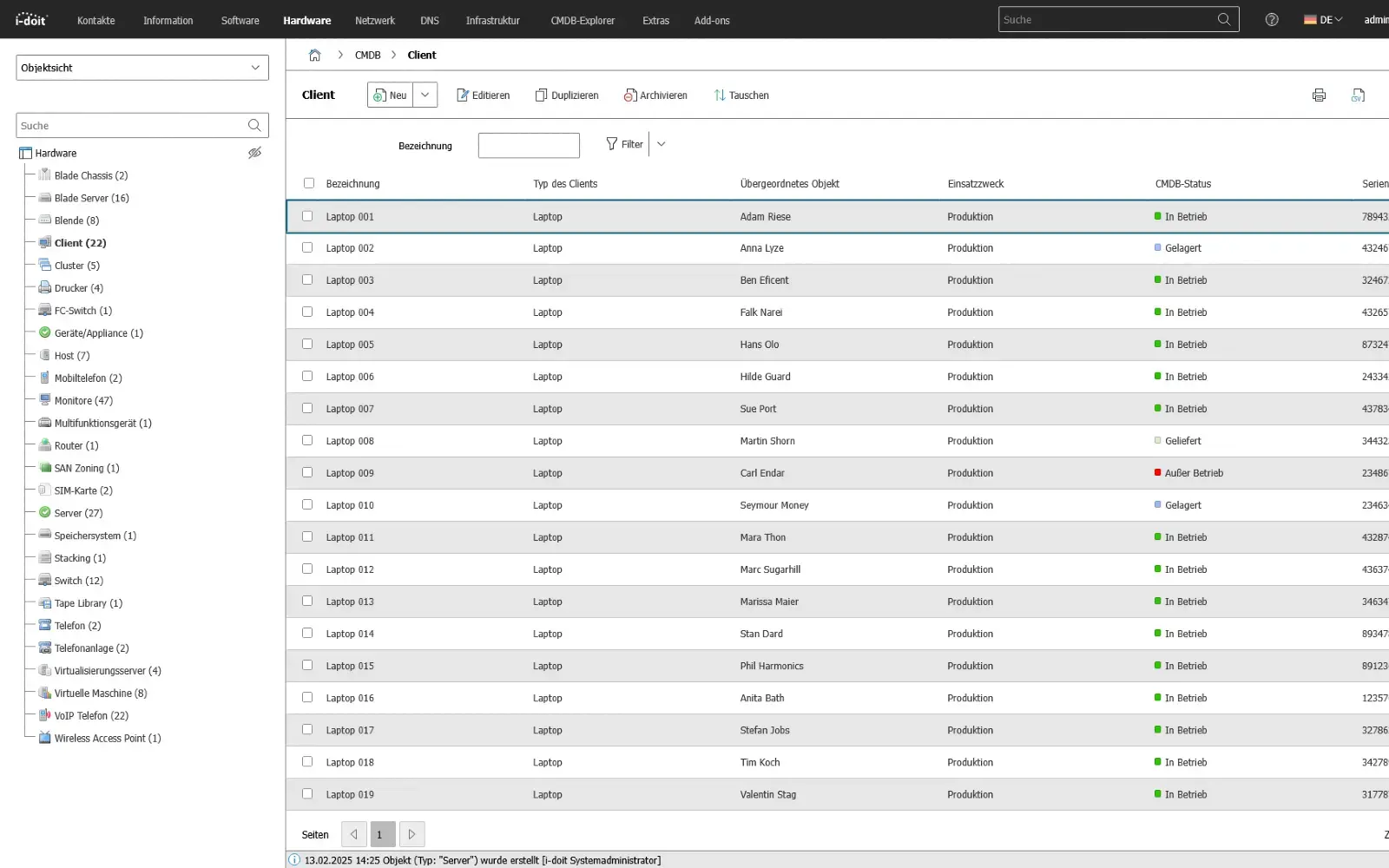
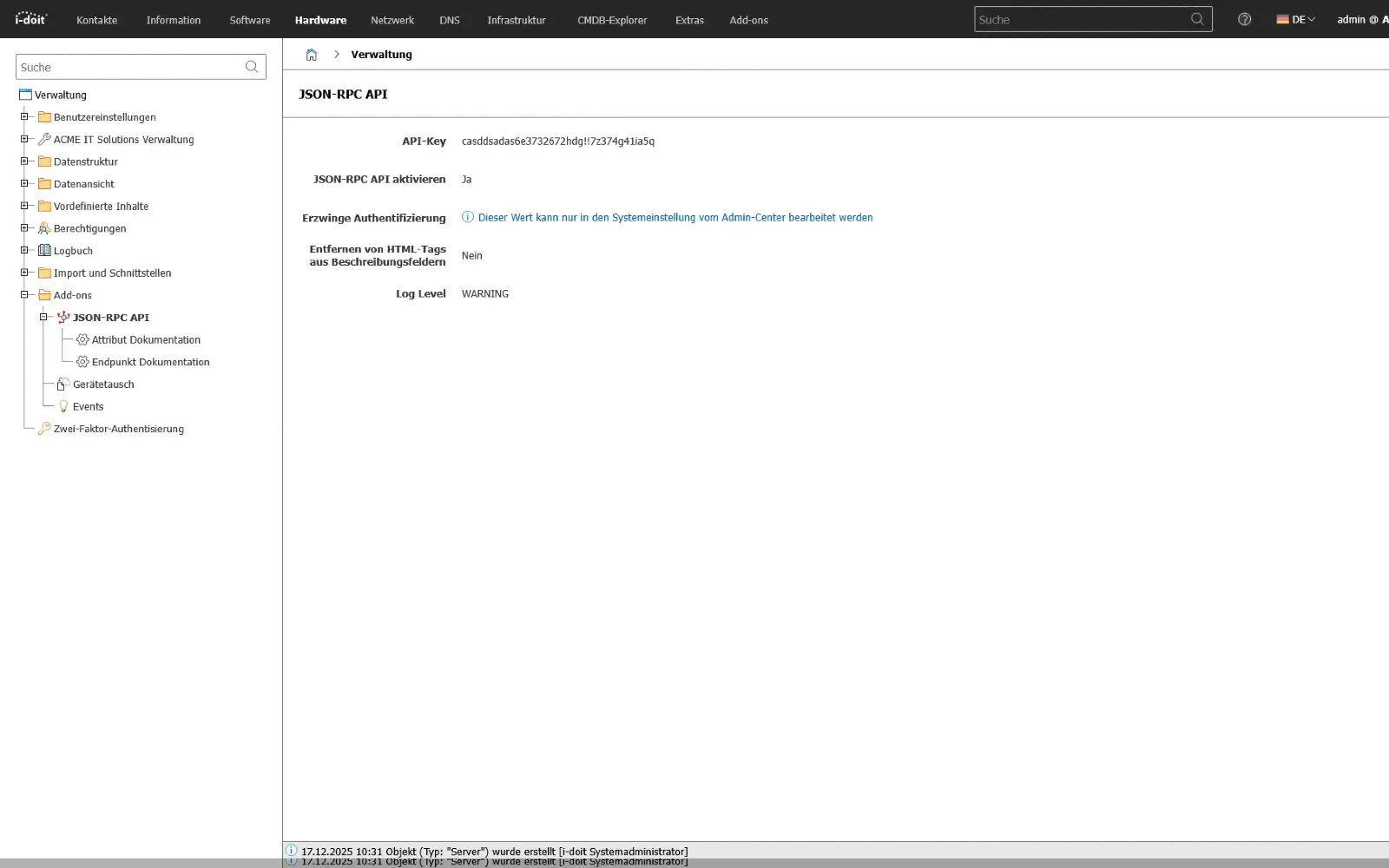
API usage - exchange data intelligently with other systems
Synchronize data between any applications and systems
With the i-doit API, you can seamlessly connect your CMDB to existing applications, services and automations. Whether ticketing, monitoring, discovery, asset management or your own business tools: Data can be exchanged bidirectionally, updated and processed in real time. This creates a central information point that connects different systems with each other and considerably simplifies processes.
Configurations, status values, object data and relationships can be automatically transferred to or from external systems. Changes made in a connected system can be immediately mapped in the CMDB - without manual effort and without duplicate data storage.
The API enables companies to flexibly expand their processes, automate workflows and make information available exactly where it is needed.
Advantages:
- Automatic data exchange between CMDB and third-party systems
- Bidirectional synchronization of assets, status values, relationships and metadata
- No duplicate maintenance thanks to a central, standardized data source
- Flexible integration into existing software landscapes and specially developed tools
- Automation of processes (e.g. creation of new tickets, discovery updates, monitoring alerts)
- Higher data quality, as information is always kept up-to-date and consistent
- Optimal basis for processes, reporting, audits and ITSM workflows