IT service management (ITSM)
Software, use cases & solutions
4.7/5 on Capterra | 2,000+ satisfied customers

What is IT service management?
Introduction
IT service management (ITSM) encompasses the complete planning, provision, control and continuous improvement of all IT services - from requests to prioritization, SLAs, change processes, service level monitoring and the structured processing of incidents and service requests.
Unlike pure ticket processing, ITSM goes far beyond "Who cares?" and answers "What services do we deliver? With which SLAs? What dependencies exist? What risks arise? How efficiently do we work? How satisfied are the users?".
With i-doit Service Management, you can manage services, assets, support contracts, SLAs, changes, incidents, configuration data, locations, responsibilities and complete service relationships - including history, workflows, escalations and auditability.
IT teams gain transparency, service quality and controllability instead of just processing tickets.
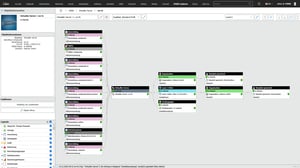
Use cases
Use cases relating to ISMS, risk and compliance management

You control audits centrally, plan audits, document results and automatically generate audit reports.

You can manage documents in an audit-proof manner, version and edit them directly in the tool and use templates and import functions.

i-doit supports GAP analyses according to standards such as ISO 27001, ISO 9001 or NIS2, including maturity level assessment, responsibilities and document assignment.

You evaluate and manage suppliers centrally, document contracts and maintain contact details and replacement suppliers.

You derive measures, distribute tasks, track deadlines and receive automatic notifications by e-mail.

You document and evaluate security incidents in accordance with ISO and NIS2, assign affected assets and centrally derive measures.
How is IT service management structured?
Efficient IT service management is based on a consistent information base on devices, software, locations, users and dependencies. i-doit provides this information in a structured manner and links it to processes and tools that are used in daily operations.
The integration of discovery systems, monitoring solutions and ticketing tools creates a uniform basis for support, operation, maintenance and continuous improvement. i-doit thus becomes a central information system that supports the entire life cycle of IT services.
Advantages:
- Central point of reference for all service processes: Asset, status and process data are maintained consistently in one place and are available to support, technology and management independently of each other.
- Traceable decisions during operation: histories, dependencies and responsibilities can be viewed at any time and form a reliable basis for planning, error analysis and maintenance measures.
- Reduced maintenance and coordination effort: Automated data flows from discovery and monitoring minimize manual updates and prevent data disruptions between teams and tools.
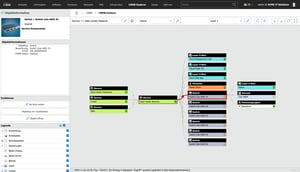
How to integrate ticketing into your CMDB
Link processes, faults and tasks with assets
By connecting a ticket system, i-doit becomes the central source of information for IT support. When a ticket is created, all relevant data on the affected device, user or service is immediately available - including history, faults, software versions and contracts. Processes can be linked directly to the associated assets so that support and technology work with the same database. The bidirectional exchange automatically keeps all information up to date and reduces manual effort.
Advantages:
- Faster error analysis: All relevant asset and user information is directly available with the ticket, which means that causes can be identified more quickly.
- Standardized information: Support, technology and management work with the same database thanks to the direct linking of tickets and CMDB objects.
- Automated up-to-dateness: Bidirectional synchronization keeps master data, status and changes up to date without manual effort.
Discovery & network inventory
Automated network inventory for consistent data quality and minimized maintenance effort
A discovery tool automatically inventories your network and keeps the CMDB i-doit up to date without any manual effort. Devices, changes and new systems are recognized, transferred in a structured manner and assigned directly to the appropriate objects. Shadow IT becomes visible, data remains consistent and the maintenance effort is significantly reduced.
Advantages:
- Automatic updating: New devices and changes are adopted directly without manual maintenance.
- Increased transparency: Hidden systems and shadow IT are visible and clearly documented.
- Significantly less effort: Inventory, reconciliation and updates run in the background with minimal personnel input.
Why integrate monitoring?
Link operating states and events with your documentation
Monitoring systems determine the status of systems and services in real time. Thanks to the link with i-doit, these statuses are not viewed in isolation, but in the context of the documented assets.
Warnings, threshold values and availabilities therefore relate to specific devices, servers, applications or network segments. The collected status information supplements the documentation and forms a reliable basis for planning, troubleshooting and service quality.
Advantages:
- Current operating data visible on the affected assets
- Identification of faults with reference to locations or dependencies
- Conclusions on bottlenecks or recurring faults
- Support for trend analyses, maintenance cycles and capacity planning

Industries
View all solutions for your industry



Read more




How to use i-doit as a central tool for IT service management.
responsibilities
systems
and document processes
1. Record infrastructure, services and responsibilities
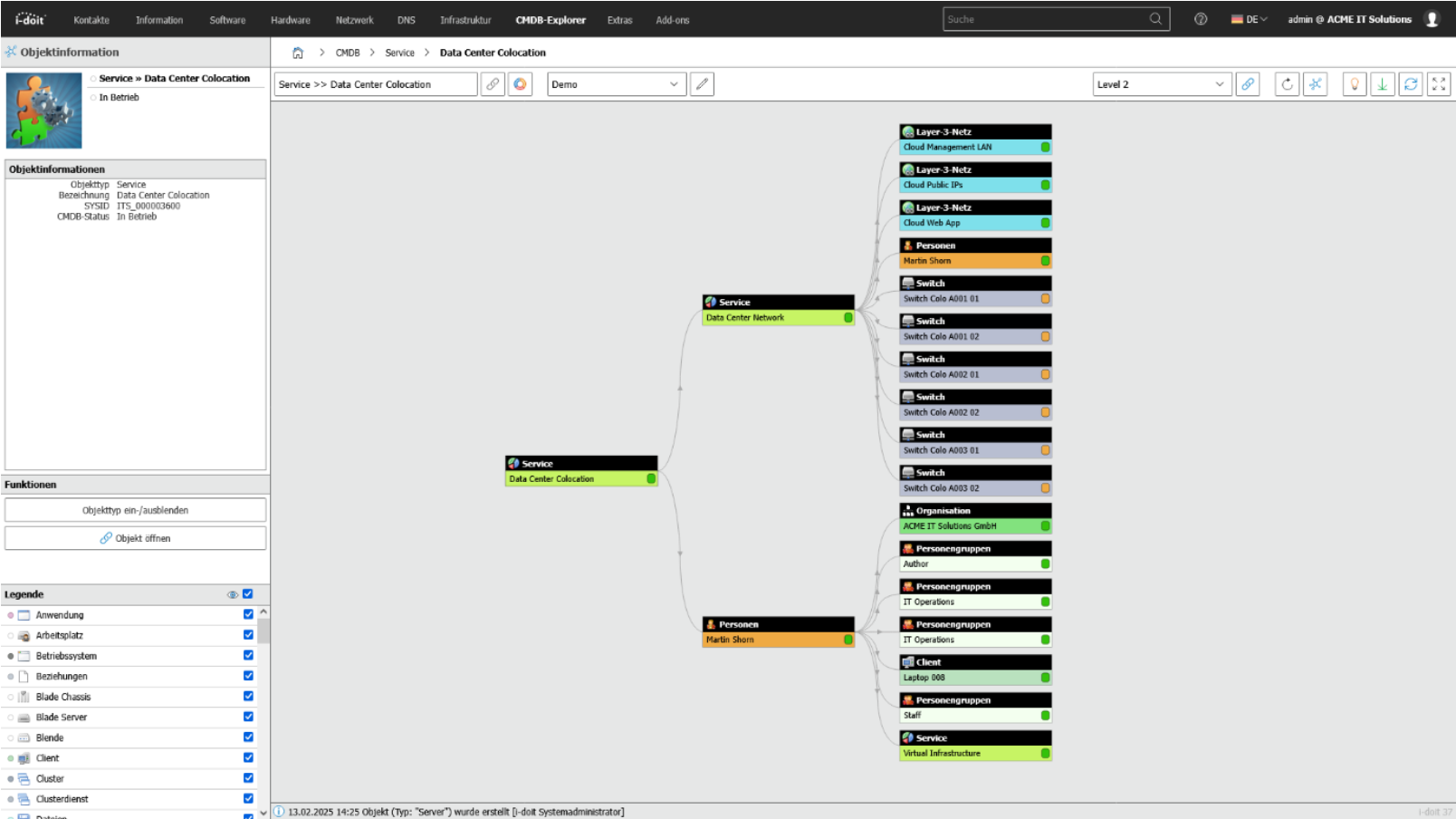
The first step is to create all relevant information about your IT landscape in i-doit in a structured manner. This includes devices, software, virtual systems, locations, users and service dependencies. Each element is mapped as a separate object with clearly defined attributes and has its own history.
This uniform object structure creates a reliable information basis that functions independently of tables, individual knowledge or local documents. Responsibilities, roles and service groups can be assigned directly, which means that the entire context of an asset - from technical structure to organizational responsibility - remains visible and can be used later in service processes.
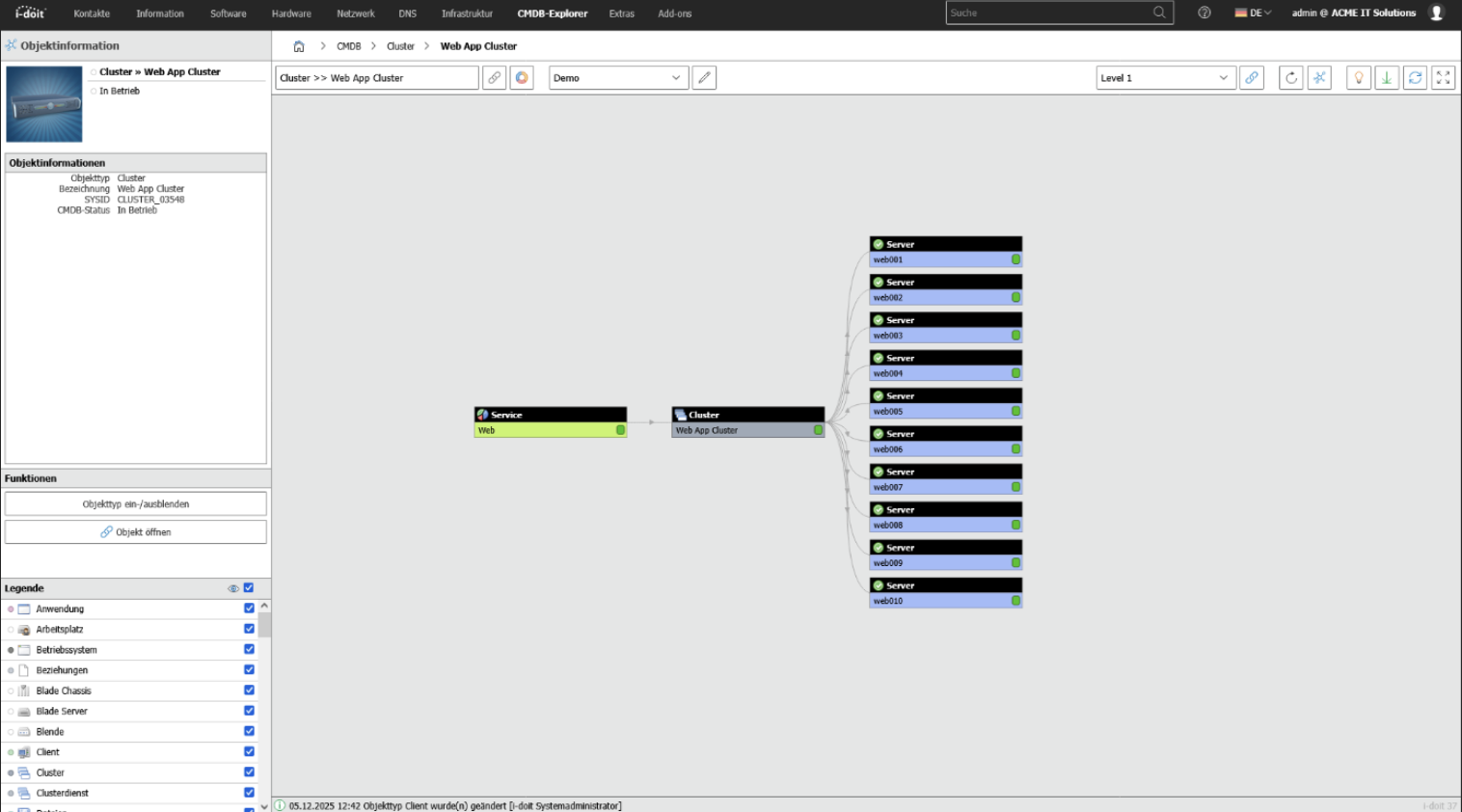
2. Connect discovery and monitoring systems
In the second step, existing discovery and monitoring tools are connected to i-doit. Discovery systems automatically record inventory and configuration data and transfer it to the documentation in a structured manner. Monitoring solutions provide operating states, warnings and events that are directly linked to the assets concerned.
This creates a continuously updated image of your IT environment that not only registers changes, but also makes their significance comprehensible. New devices, changed configurations or failures are therefore not viewed in isolation, but in the context of the documented infrastructure, services and responsibilities.
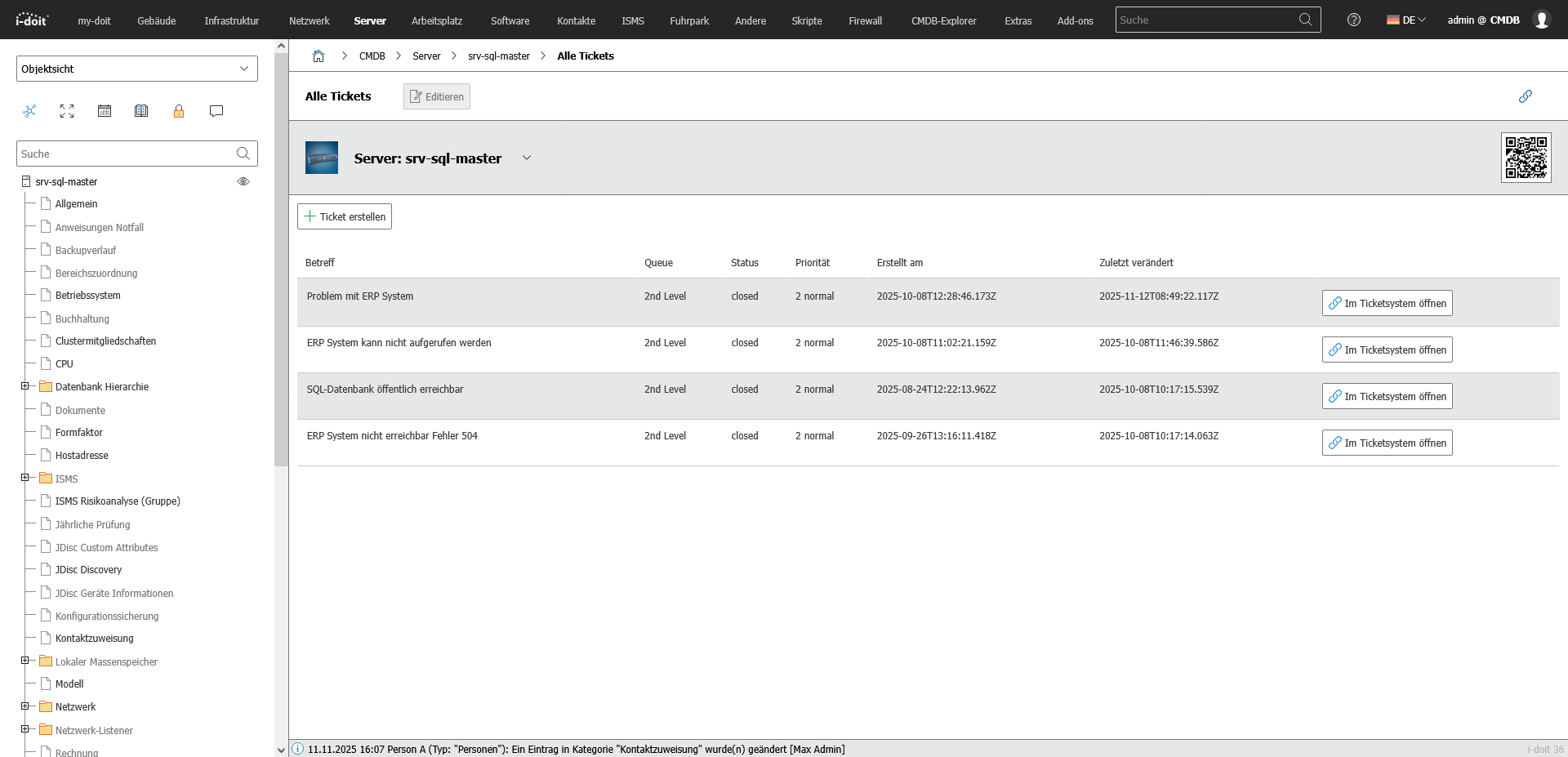
3. Connect ticketing processes and document procedures
In the third step, the ticketing system is integrated into ongoing operations. Support, maintenance and change requests can be linked directly to the affected assets, locations or services. Each ticket thus not only supplements the operational process, but also extends the documentation of the service life cycle.
Faults, causes, measures and decisions remain traceable and are permanently assigned to the respective object. This creates a complete picture of the history of devices and services - from commissioning to decommissioning - and support, technology and management have access to the same level of information at all times.
Additional applications
(KRITIS, ISO27001 and NIS2)
and system manuals
third-party systems (API)
QR codes
end devices
1. Maintain compliance (KRITIS, ISO27001 and NIS2)
Ensure compliance with laws, standards and directives with a CMDB.
With i-doit, risks according to ISO 27001 can be systematically recorded, evaluated and linked to the affected assets. This creates a transparent basis for the verification of security measures and the implementation of NIS2 requirements. Technical and organizational measures (TOMs) are centrally documented, monitored and maintained in an audit-proof manner.
Advantages:
- Auditable company divisions
- Audit-proof recording in accordance with NIS2 & ISO-27001 & BSI-KritisV
- Strengthening of information security,
- Implementation of PDCA processes
- Faster response in the event of an incident or crisis
2. IT concepts, emergency and system manuals
Create, link and maintain operational and emergency documentation in a structured and audit-proof manner.
With the i-doit CMDB, companies can create and maintain all important technical documentation in a complete, up-to-date and audit-proof manner. i-doit enables the structured creation of emergency manuals, system manuals, operating concepts and guidelines. These can be linked directly to the associated assets, processes and locations. As a result, all documentation is automatically fed with real statuses from the IT landscape and remains permanently consistent.
All relevant information such as responsibilities, operating parameters, dependencies, restart processes and recovery times (RTO/RPO) are maintained and versioned centrally. The connection to infrastructure, applications and services means that documentation is not only maintained, but actively lived and constantly kept up to date. This is one of the most important factors for audits, certifications and operational stability.
Advantages:
- Centralized, versioned and audit-proof documentation
- Clear responsibilities and traceable operating processes
- Audit and audit-proof evidence in accordance with ISO 27001, NIS2 and BSI requirements
- Faster restart times in an emergency thanks to clear, always up-to-date instructions
- Transparent dependencies between systems, processes and services
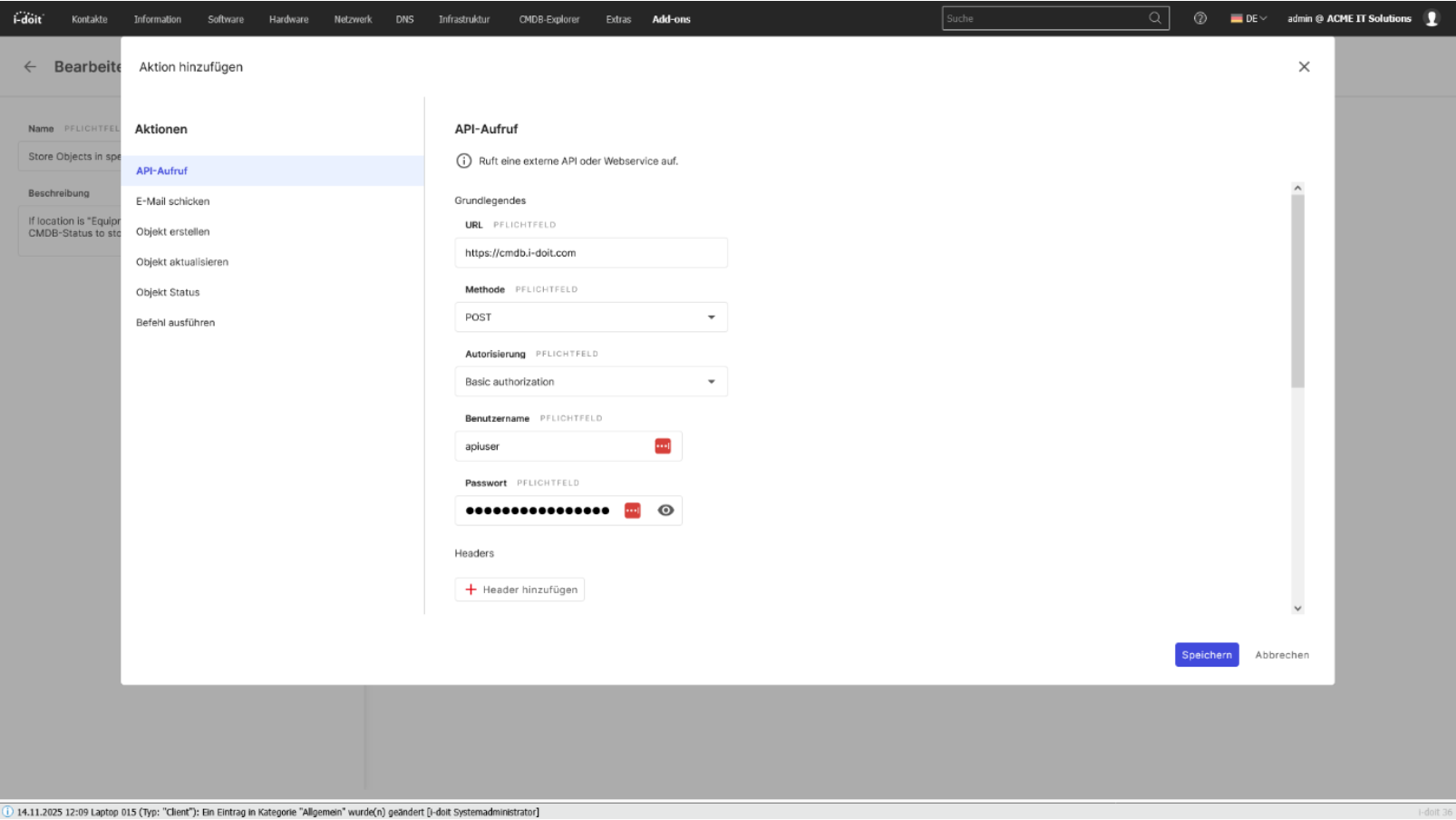
3. Connection of third-party systems (API)
Connect systems automatically and exchange data seamlessly between applications.
With the i-doit API, you can seamlessly connect your CMDB to existing applications, services and automations. Whether ticketing, monitoring, discovery, asset management or your own business tools: Data can be exchanged bidirectionally, updated and processed in real time. This creates a central information point that connects different systems with each other and considerably simplifies processes.
Configurations, status values, object data and relationships can be automatically transferred to or from external systems. Changes made in a connected system can be immediately mapped in the CMDB - without manual effort and without duplicate data storage.
The API enables companies to flexibly expand their processes, automate workflows and make information available exactly where it is needed.
Advantages:
- Automatic data exchange between CMDB and third-party systems
- Bidirectional synchronization of assets, status values, relationships and metadata
- No duplicate maintenance thanks to a central, standardized data source
- Flexible integration into existing software landscapes and specially developed tools
- Automation of processes (e.g. creation of new tickets, discovery updates, monitoring alerts)
- Higher data quality, as information is always kept up-to-date and consistent
- Optimal basis for processes, reporting, audits and ITSM workflows
4. Inventory with QR codes
Immediately record and identify assets on site and update them directly in the CMDB.
With the i-doit CMDB, the entire inventory process can be digitized and considerably simplified through the use of QR codes. Each asset, from servers and network components to mobile devices, furniture or tools, is given a unique QR code that links directly to the assets in i-doit. This makes information immediately available on site and changes can be recorded directly on the asset.
Mobile devices can be used to update hardware, software versions, locations, responsibilities or maintenance information quickly and without errors. The QR code function supports internal processes as well as audits, inventory checks and lifecycle-based documentation.
Advantages:
- Fast, local inventory using a smartphone or tablet
- Reduced error rate thanks to automated allocation
- Centrally maintained data as the basis for audits and ITSM processes
- Transparent documentation of location and status changes
- Ideal for inventories, relocations, technology changes and lifecycle-based processes
5. Management of mobile devices
Centrally control, document and securely manage smartphones, tablets and laptops.
With i-doit, mobile devices such as smartphones, tablets, laptops and accessories can be managed centrally, completely and in an audit-proof manner. All relevant information - from serial numbers and contracts to installed apps and security guidelines - is clearly recorded and linked to users, locations and services. This allows companies to maintain an overview of inventories, responsibilities and lifecycles at all times.
By linking to MDM systems, inventory tools or Active Directory, devices can be automatically synchronized and kept up to date. Guidelines, security requirements and compliance specifications are documented transparently and mapped with the respective assets. Failures, losses and device changes can be efficiently tracked and managed.
Advantages:
- Transparent management of all mobile devices in the company
- Reduced risks thanks to documented security and compliance requirements
- Automatic updating via MDM or AD interfaces
- Faster processes for onboarding, device replacement or loss cases
- Central database as a basis for audits, ITSM and budget planning
.png?width=300&name=Contact%20(1).png)
Book your personal live demo
Our i-doit team will be happy to take the time to advise you personally on your application.
Integrations
i-doit can be seamlessly connected to IT service desk systems to optimize your support processes. Examples of compatible systems are ((OTRS)) Community Edition, KIX Service Management and Zammad.
Thanks to its flexible API, i-doit can be integrated with numerous software solutions, including ERP systems.
To automatically add data and assets to your i-doit system, we recommend the use of specialized inventory systems such as JDisc or OCS.
With i-doit, you can document your network topology clearly and in detail and include integrations.
For centralized and secure user and rights management, i-doit can be integrated into directory services such as LDAP or Active Directory.
i-doit is made for the joint operation of monitoring systems. Examples here are: Nagios or Checkmk.
Suitable add-ons
Our add-ons for modular function expansion
Create powerful automations without programming knowledge, simply start them on a schedule or manually at the touch of a button.
Get 4 powerful add-ons for the price of 2! Flows, Documents, Analysis and Forms.
Automatically create documents as PDFs with daily updated data (e.g. hardware handover certificate or disaster recovery plan).
Automate the operation of your data center with the latest data from the CMDB. Events trigger and control further processes.
The maintenance add-on supports the planning, execution and documentation of maintenance and inspections. Maintenance intervals, dates and responsibilities are managed centrally and linked directly to the respective devices, installations or systems.
With the API add-on, data can be automatically read, written and updated in i-doit. Perfect for integrations with ticket systems, inventory tools or your own automations.
Add-on for powerful data analysis. Calculate service costs, check the data quality of the CMDB and carry out failure simulations.
Easily create forms that you can make available to users for simplified data entry. Example: Allow users to document hardware or goods themselves.
Set up an information security management system with risk analysis and management in accordance with ISO 27001.
Integrate the Checkmk2 monitoring system into i-doit. This supports comparisons between TARGET and ACTUAL from CMDB and monitoring.
Store buttons with your own triggers and start IT processes directly from i-doit - e.g. the automatic deployment of a virtual machine.
With this add-on, you can create an information security management system (ISMS) in accordance with the BSI's IT baseline protection methodology.




