ISMS
i-doit / Paid
Build an information security management system with risk analysis and management according to ISO 27001
-
ISO27001 Risk Management within i-doit
-
Importing and managing threats and measures from external catalogs
-
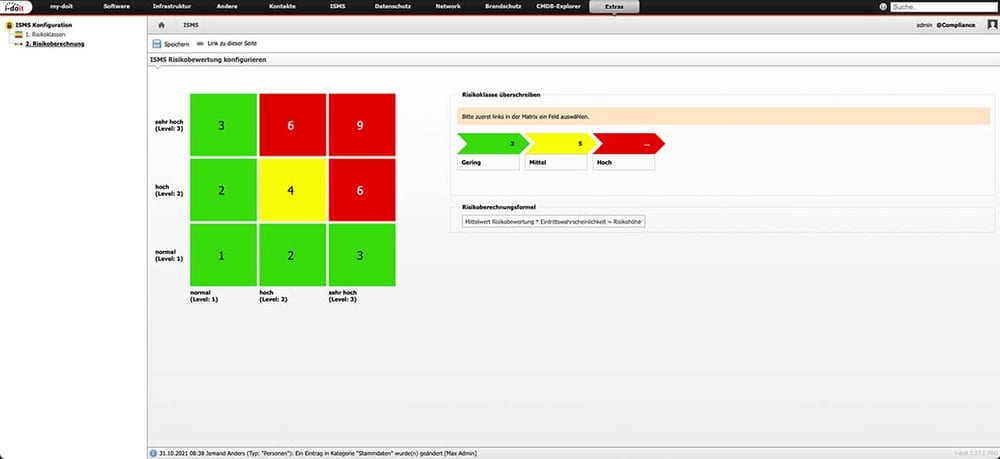
Risk evaluations directly at documented assets
-
Reporting and integration into the i-doit Add-on Documents
Information on support options can be found on the developer website
For installation instructions, please contact the developer
IT Documentation with i-doit: the foundation for successful ISMS
Get a comprehensive overview of your (IT) infrastructure while maintaining high data quality through integrated processes.
The i-doit Add-on ISMS integrates security documentation directly into your CMDB, where it belongs. Since IT documentation is the first to know about new components and infrastructure changes, you can manage security assessments daily through risk identification and evaluation of objects (IT assets, Configuration Items) directly in i-doit.
We believe change processes are complex enough already! Avoid purchasing additional software and maintaining redundant data. The i-doit Add-on ISMS's native i-doit integration leverages existing functions like templates, bulk processing, and reporting. Users can add security information to assets without modifying the underlying data model. For final refinements to your Risk Management Process, the i-doit Add-on Documents can incorporate ISMS data into professionally formatted documents matching your corporate design.
Achieve ISO 27001 Compliance in Just Three Steps
With the i-doit Add-on ISMS, you seamlessly integrate risk assessment directly into your IT asset management. Whether following ISO 27001 Annex A, the BSI IT-Grundschutz Catalog, or the IT Security Catalog of the Bundesnetzagentur, you’re covered from the start.
- Step 1: Install the i-doit Add-on ISMS and conduct risk assessments within the context of your IT assets.
- Step 2: Customize your risk management framework by adjusting predefined catalogs, defining impact scenarios, setting up mitigation measures, and assigning roles, responsibilities, and rating scales. Initial report definitions complete this phase.
- Step 3: Implement and maintain risk management to ensure ISO 27001 compliance. Analyze and evaluate assets, manage versioning, and follow the PDCA cycle (Plan, Do, Check, Act) with full documentation support from the i-doit Add-on ISMS.

Use-Cases
.webp?width=300&name=multi-ethnic-colleagues-working-together-at-data-c-2025-03-15-19-35-44-utc%20(1).webp)
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Related Add-ons
Add-on für mächtige Datenanalyse. Berechnen Sie Servicekosten, prüfen Sie die Datenqualität der CMDB und führen Sie Ausfallsimulationen durch.
Erstellen Sie leistungsstarke Automatisierungen ohne Programmierkenntnisse ganz einfach nach einem Zeitplan oder manuell per Knopfdruck starten.
Bauen Sie ein Information-Security-Management-System mit Risikoanalyse und -management nach ISO 27001 auf.
Dokumente auch als PDF automatisch erstellen mit tagesaktuellen Daten (z.B. Hardware-Übergabeschein oder Desaster Recovery Plan).
Integrieren Sie das Monitoring-System Checkmk2 in i-doit. Abgleiche zwischen SOLL und IST aus CMDB und Monitoring werden damit unterstützt.
Erstellen Sie auf einfache Weise Formulare, die Sie Nutzern zur vereinfachten Dateneingabe zur Verfügung stellen. Beispiel: Hardware oder Waren selbst dokumentieren lassen.
Hinterlegen Sie Buttons mit eigenen Triggern und starten Sie IT-Prozesse direkt aus i-doit –z.B. das automatische Deployen einer virtuellen Maschine.
Mit diesem Add-on können Sie ein Managementsystem für die Informationssicherheit (ISMS) nach IT-Grundschutz-Methodik des BSI erstellen.
Get your personalized quote today!
Discover how the i-doit Add-on ISMS can support and streamline your processes. Get in touch with us for more information, pricing details, or to request a quote.

Telefon: +49 (0) 211 - 699 31 0

