Software and license management
With i-doit, you can document software products, versions, installations, license models and contract terms centrally and in an audit-proof manner.
You can keep track of license costs, responsibilities, compliance obligations and risks.
4.7/5 on Capterra | 2,000+ satisfied customers

The 6 most important functions for software and license management
All applications used are recorded centrally and logically assigned to the respective devices, servers or VMs.
Licenses, quantities and usage are documented centrally so that license models are clearly traceable.
Software and license data can be exported as clear evaluations. Automatic notifications provide timely information about expiring licenses.
Versions, patch statuses and release information can be clearly displayed for each software and device.
License usage, validity and contract information are stored in an audit-proof manner and can be checked at any time.
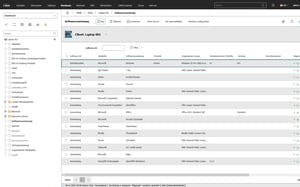
Full overview of software & installations
How can software and licenses be clearly recorded and assigned?
Software and licenses are often managed separately or incompletely. As a result, there are no clear assignments to installations, users or devices - and the actual license requirements remain unclear.
i-doit enables the structured recording of software and licenses and their clear allocation to installations, devices and users. All relationships are documented centrally and can be traced at any time.
Advantages:
- Clear assignment of licenses to software installations
- Transparent display of usage and license inventory
- Less manual maintenance work
- Better decision-making basis for license management
Manage licenses centrally
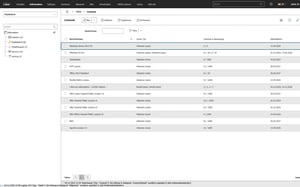
How can licenses be clearly recorded and assigned?
Licenses are often managed in isolation, without clear allocation to installations, devices or users. This makes it difficult to maintain an overview and increases the risk of under- or over-licensing.
i-doit enables the structured recording and clear allocation of licenses to software installations, devices, users or organizational units. All correlations are centrally documented and can be traced at any time.
Advantages:
- Clear assignment of licenses to installations and users
- Transparent presentation of license inventories and usage
- Reduced administrative effort thanks to structured maintenance
- Reliable basis for license decisions
Automatic notifications
How do you recognize under-, over- and mislicensing at an early stage?
Without systematic evaluation, license deviations often remain undetected for a long time. This leads either to unnecessary costs or to compliance risks - especially during audits.
i-doit automatically analyzes the license status and transparently displays discrepancies between existing licenses and actual usage. Under-, over- and mislicensing become visible at an early stage.
Advantages:
- Early detection of license discrepancies
- Avoidance of unnecessary license costs
- Reduction of audit and compliance risks
- Sound basis for subsequent licensing or reduction

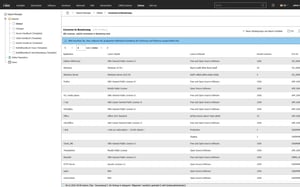
Auditable license documentation
How do you keep an eye on runtimes, maintenance and subscription models?
Modern software is increasingly being purchased via maintenance contracts or subscription models. Without a central overview, terms, renewals or notice periods are easily overlooked.
i-doit documents license terms, maintenance periods and contract models centrally and monitors them automatically. This enables timely and well-founded decisions to be made.
Advantages:
- Centralized management of terms and subscriptions
- Timely information about renewals and deadlines
- Avoidance of unwanted contract extensions
- Better planning of license decisions
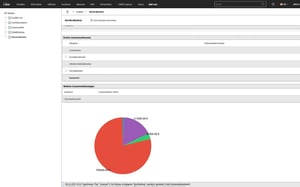
Clear budget and cost control
How do you achieve clear budget and cost control?
Without transparency about license costs, maintenance fees and subscriptions, there is no basis for effective controlling. Potential savings remain hidden and budgets are planned inaccurately.
i-doit links software and licenses with costs, budgets and cost centers. In this way, expenditure can be analyzed, compared and controlled in a targeted manner - audit-proof and traceable.
Advantages:
- Transparent allocation of license costs to cost centers
- Improved budget planning and cost control
- Identification of potential savings
- Reliable decision-making basis for purchasing and management
.png?width=300&name=Contact%20(1).png)
Book your personal live demo
Our i-doit team will be happy to take the time to advise you personally on your application.
Suitable add-ons
Our add-ons for modular function expansion
Create powerful automations without programming knowledge, simply start them on a schedule or manually at the touch of a button.
Get 4 powerful add-ons for the price of 2! Flows, Documents, Analysis and Forms.
Automatically create documents as PDFs with daily updated data (e.g. hardware handover certificate or disaster recovery plan).
Automate the operation of your data center with the latest data from the CMDB. Events trigger and control further processes.
The maintenance add-on supports the planning, execution and documentation of maintenance and inspections. Maintenance intervals, dates and responsibilities are managed centrally and linked directly to the respective devices, installations or systems.
With the API add-on, data can be automatically read, written and updated in i-doit. Perfect for integrations with ticket systems, inventory tools or your own automations.
Add-on for powerful data analysis. Calculate service costs, check the data quality of the CMDB and carry out failure simulations.
Easily create forms that you can make available to users for simplified data entry. Example: Allow users to document hardware or goods themselves.
Set up an information security management system with risk analysis and management in accordance with ISO 27001.
Integrate the Checkmk2 monitoring system into i-doit. This supports comparisons between TARGET and ACTUAL from CMDB and monitoring.
Store buttons with your own triggers and start IT processes directly from i-doit - e.g. the automatic deployment of a virtual machine.
With this add-on, you can create an information security management system (ISMS) in accordance with the BSI's IT baseline protection methodology.
Related use cases
i-doit offers companies comprehensive functions and interfaces

You connect ticket systems, automation tools and monitoring systems such as Zammad or n8n directly via API.

You document workstations with devices, peripherals and responsible persons and control handovers and returns centrally.

You control audits centrally, plan audits, document results and automatically generate audit reports.

You analyze your IT infrastructure, identify documentation gaps and create location, user or cost centre-related reports and audit PDFs.

You are automatically informed about deadlines, licenses and guarantees and can keep an eye on the status and need for action.

You automatically record clients, servers, printers and peripherals and document hardware, software and QR codes centrally.

You manage users, accounts and rights centrally, document responsibilities and control access per system, including LDAP and group connections.

You document data protection incidents in compliance with the GDPR, assess risks and derive measures centrally.

You can manage documents in an audit-proof manner, version and edit them directly in the tool and use templates and import functions.

You create technical and organizational restart plans with automatic calculation of the restart times.

i-doit supports GAP analyses according to standards such as ISO 27001, ISO 9001 or NIS2, including maturity level assessment, responsibilities and document assignment.
You link tickets to affected devices, analyze causes via dependencies and monitor SLAs centrally.

You record and uniquely identify assets using QR and barcodes, create individual labels and take a mobile inventory of devices using the app and printer tool.

You document emergency concepts, system manuals, backups and disaster recovery centrally and comprehensibly.

They document maintenance and lifecycles, make changes traceable, automate processes and keep track of responsibilities and warranty periods.

You evaluate and manage suppliers centrally, document contracts and maintain contact details and replacement suppliers.

You derive measures, distribute tasks, track deadlines and receive automatic notifications by e-mail.

You integrate monitoring data directly into the IT documentation, see asset failures and link statuses to the change history.

You document active and passive network elements including cabling, port assignment, IP addresses and configurations centrally and comprehensibly.

You manage entries and exits, including device handovers, returns and referral certificates centrally.

i-doit enables protection requirement analyses with automatic inheritance into the infrastructure, risk assessment and tracking of measures.

You document and evaluate security incidents in accordance with ISO and NIS2, assign affected assets and centrally derive measures.

You record and analyze software and licenses, monitor runtimes, users and authorizations and avoid license violations and unnecessary costs.

You document locations, rooms and infrastructure, link these to contact persons and also visualize server rooms clearly.

You document and manage contracts centrally, link them to objects and responsible parties and are automatically informed about deadlines and terms.

You keep an eye on servers, VMs, dependencies and certificates centrally and automatically synchronized.




